Author: Wasim Khan Sujon
-

How to Become a Certified Ethical Hacker: Step-by-Step Guide
To become a Certified Ethical Hacker, complete the EC-Council’s CEH training and pass the CEH exam. Prior experience in IT security is recommended. How to Become a Certified Ethical Hacker:Ethical hacking plays a crucial role in safeguarding digital assets. As cyber threats increase, the demand for skilled ethical hackers rises. Certification in ethical hacking validates
-
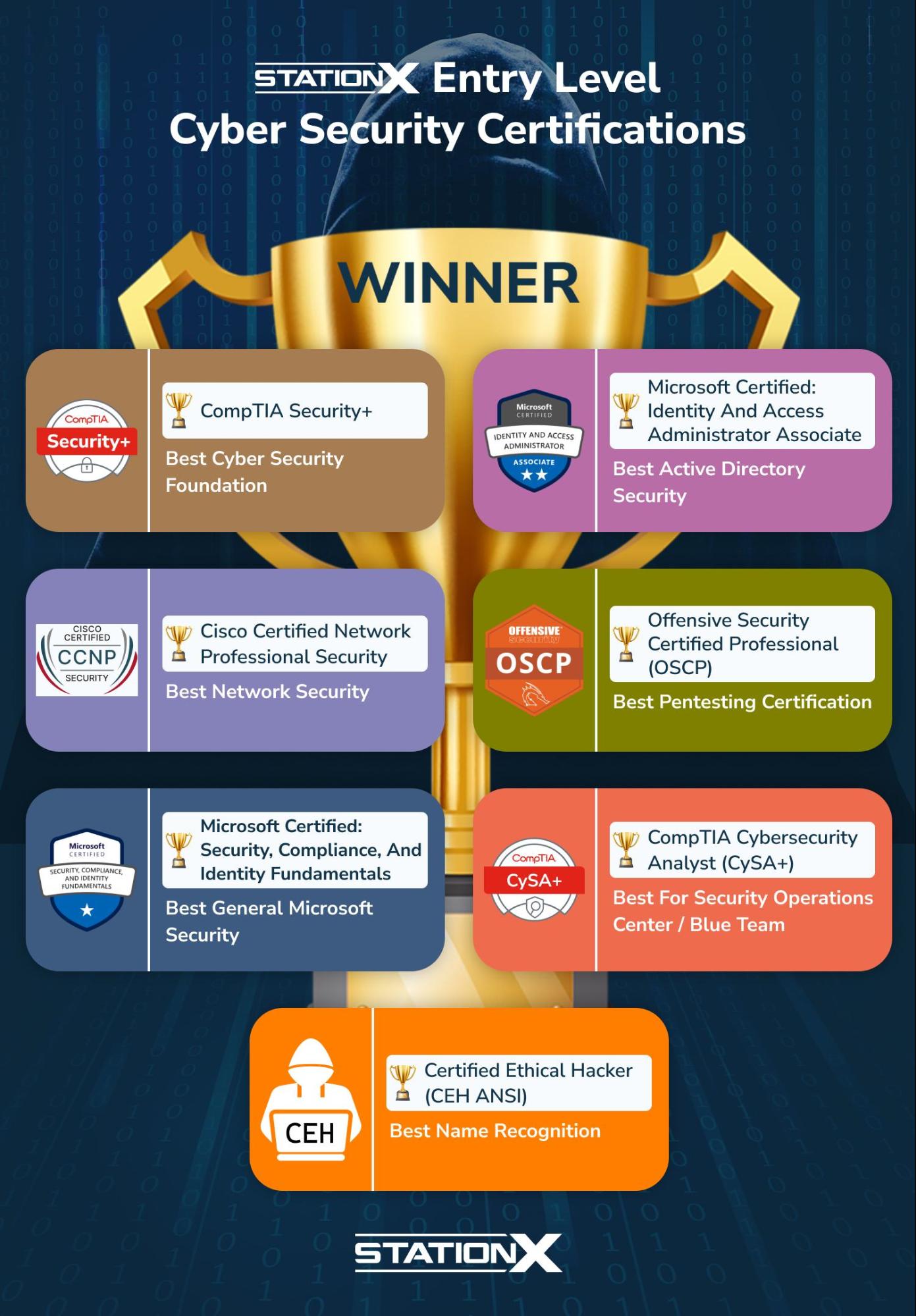
Top Cybersecurity Certifications for Beginners: Elevate Your Skills!
Top cybersecurity certifications for beginners include CompTIA Security+, Certified Ethical Hacker (CEH), and Cisco’s CCNA Security. These certifications provide foundational knowledge and skills to start a career in cybersecurity. Cybersecurity is a rapidly growing field, essential for protecting sensitive information and systems from threats. As cyberattacks increase, the demand for skilled professionals rises. Beginners seeking
-

How to Prevent Phishing Attacks in 2024: Proactive Measures
To prevent phishing attacks in 2024, use multi-factor authentication and educate employees about recognizing suspicious emails. Regularly update security software to protect against new threats. How to Prevent Phishing Attacks in 2024:Phishing attacks continue to evolve, targeting both individuals and organizations. As technology advances, cybercriminals become more sophisticated in their tactics, making it essential to
-

Best Cybersecurity Practices for Small Businesses: Stay Safe!
**Best Cybersecurity Practices for Small Businesses:** Implement strong passwords, regular software updates, and employee training to safeguard sensitive information. Small businesses face unique cybersecurity challenges. Limited resources often make them attractive targets for cybercriminals. Establishing robust cybersecurity practices is essential for protecting valuable data. Start by training employees on recognizing phishing attacks and using strong
-

Cybersecurity Threats in 2024: Protect & Prevail
Cybersecurity threats in 2024 include advanced ransomware attacks and increased vulnerabilities in IoT devices. Organizations must prioritize proactive measures to mitigate these risks. As we navigate through 2024, the landscape of cybersecurity continues to evolve. Cybercriminals are leveraging sophisticated techniques to exploit weaknesses in systems and networks. Ransomware remains a dominant threat, targeting businesses of
-
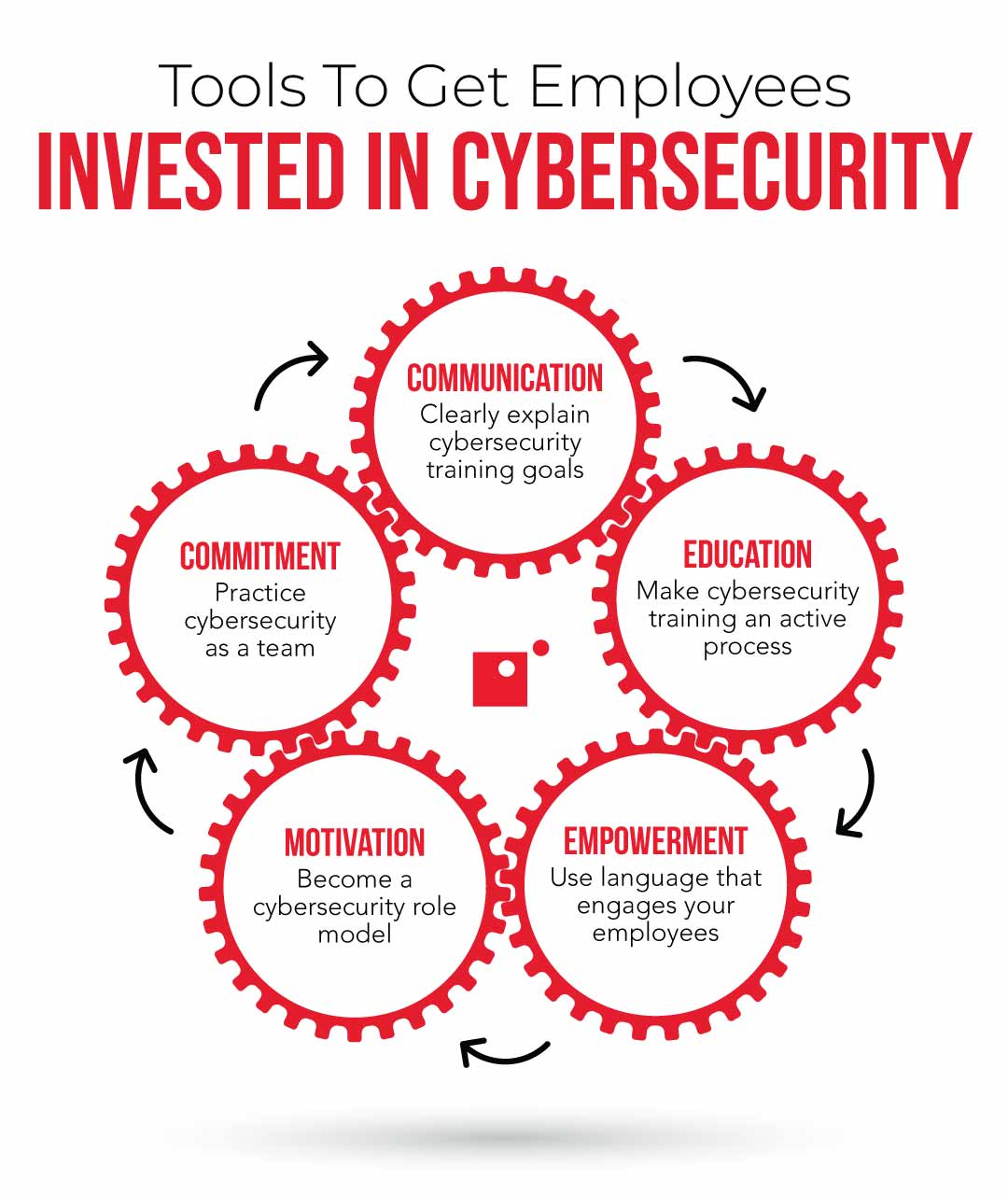
Cybersecurity Training for Employees: Enhance Your Team’s Defense!
Cybersecurity training for employees is essential for protecting sensitive information. It equips staff with skills to recognize and respond to cyber threats. As cyber threats grow increasingly sophisticated, organizations must prioritize employee training. Cybersecurity is not just the IT department’s responsibility; every employee plays a crucial role in safeguarding company data. Training programs help staff
-
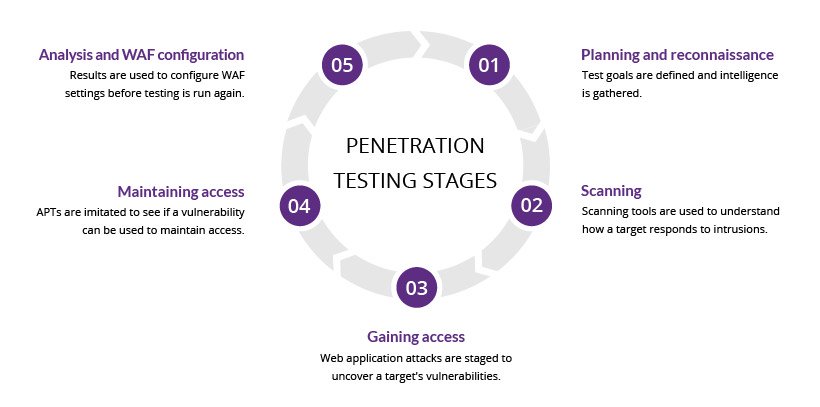
How to Conduct a Web Application Penetration Test Step by Step: A Masterclass
To conduct a web application penetration test, follow these steps: define the scope, gather information, identify vulnerabilities, exploit weaknesses, and report findings. Each step is crucial for assessing security and mitigating risks. Web application penetration testing is vital for identifying security vulnerabilities before they can be exploited. As online threats increase, organizations must ensure their
-

Penetration Testing Report Templates: Boost Your Security!
Penetration testing report templates provide a structured format to document findings and recommendations. Examples of these templates can streamline the reporting process and enhance clarity. A penetration testing report is essential for organizations seeking to strengthen their cybersecurity. It details vulnerabilities found during testing and offers actionable recommendations. Using a standardized template can improve consistency
-
How to Prepare for a Penetration Testing Engagement: Key Tactics
To prepare for a penetration testing engagement, define the scope and objectives clearly. Gather relevant documentation and ensure all stakeholders are informed. Penetration testing is vital for identifying vulnerabilities in your systems. This proactive approach helps organizations strengthen their security posture. Proper preparation sets the stage for an effective assessment. Begin by defining what assets
-
Top Penetration Testing Methodologies for Network Security: Unveiled
Top penetration testing methodologies for network security include the OWASP Testing Guide, NIST SP 800-115, and PTES. These frameworks help identify vulnerabilities effectively. Penetration testing is crucial for maintaining robust network security. It simulates real-world attacks to uncover weaknesses before malicious actors can exploit them. Various methodologies guide this process, ensuring thorough assessments and actionable
