Author: Wasim Khan Sujon
-
How to Perform Penetration Testing on Wireless Networks: A Step-by-Step Guide
To perform penetration testing on wireless networks, start by conducting a thorough network assessment. Use tools like Aircrack-ng to identify vulnerabilities and test security measures. Wireless networks are essential for modern connectivity but can be vulnerable to various attacks. Penetration testing serves as a proactive method to identify weaknesses before malicious actors exploit them. This
-
Network Security Strategies for IoT: Enhance Your Defense!
To protect IoT devices, implement strong authentication methods and regular software updates. Segregate IoT networks from critical systems to minimize risks. Network Security Strategies for IoT:The Internet of Things (IoT) has revolutionized how we interact with technology. With countless devices connecting to the internet, security vulnerabilities have increased significantly. Cybercriminals target IoT devices for sensitive
-

Best Network Security Practices for Small Businesses: Stay Safe!
Best network security practices for small businesses include implementing strong passwords and regular software updates. Additionally, employee training on phishing and other threats is crucial. Small businesses often face unique challenges in network security. Limited resources and expertise can leave them vulnerable to cyberattacks. Adopting effective security practices is essential for safeguarding sensitive information. Strong
-

Common Network Security Vulnerabilities: Proactive Fixes
Common network security vulnerabilities include weak passwords, outdated software, and unpatched systems. Fix them by implementing strong password policies, regular updates, and robust firewall protections. Network security is crucial in today’s digital landscape. With cyber threats evolving rapidly, businesses must prioritize safeguarding their data and systems. Common vulnerabilities can lead to devastating breaches if left
-
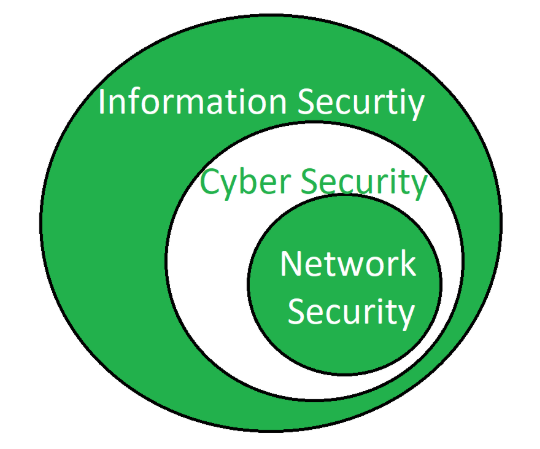
Difference between Network Security And Cybersecurity: Key Insights
Network security focuses on protecting the integrity, confidentiality, and availability of data within a network. Cybersecurity encompasses a broader scope, addressing threats to all digital assets, including software and hardware. Difference between Network Security And Cybersecurity:Understanding the difference between network security and cybersecurity is crucial for businesses and individuals. As technology evolves, so do the
-

Network Security Solutions for Cloud-Based Environments: Fortify Now!
Network security solutions for cloud-based environments include firewalls, encryption, and identity management systems. These measures protect data integrity and prevent unauthorized access. Cloud computing has revolutionized how businesses operate, offering flexibility and scalability. However, this shift has brought new security challenges. Organizations must prioritize robust security solutions tailored for cloud environments. Effective network security is
-

How to Register a Domain Name for Free: Insider Tips
To register a domain name for free, use a free domain provider like Freenom. You can also find promotional offers from web hosting services. How to Register a Domain Name for Free:Registering a domain name is a crucial step for anyone looking to establish an online presence. A memorable domain enhances credibility and helps attract
-

What is Domain Name Privacy Protection? Secure Your Identity!
Domain Name Privacy Protection safeguards your personal information from public access in the WHOIS database. It’s crucial for maintaining privacy and reducing spam. What is Domain Name Privacy Protection:Registering a domain is an essential step for establishing an online presence. However, this process often exposes personal details like your name, address, and phone number. Without
-
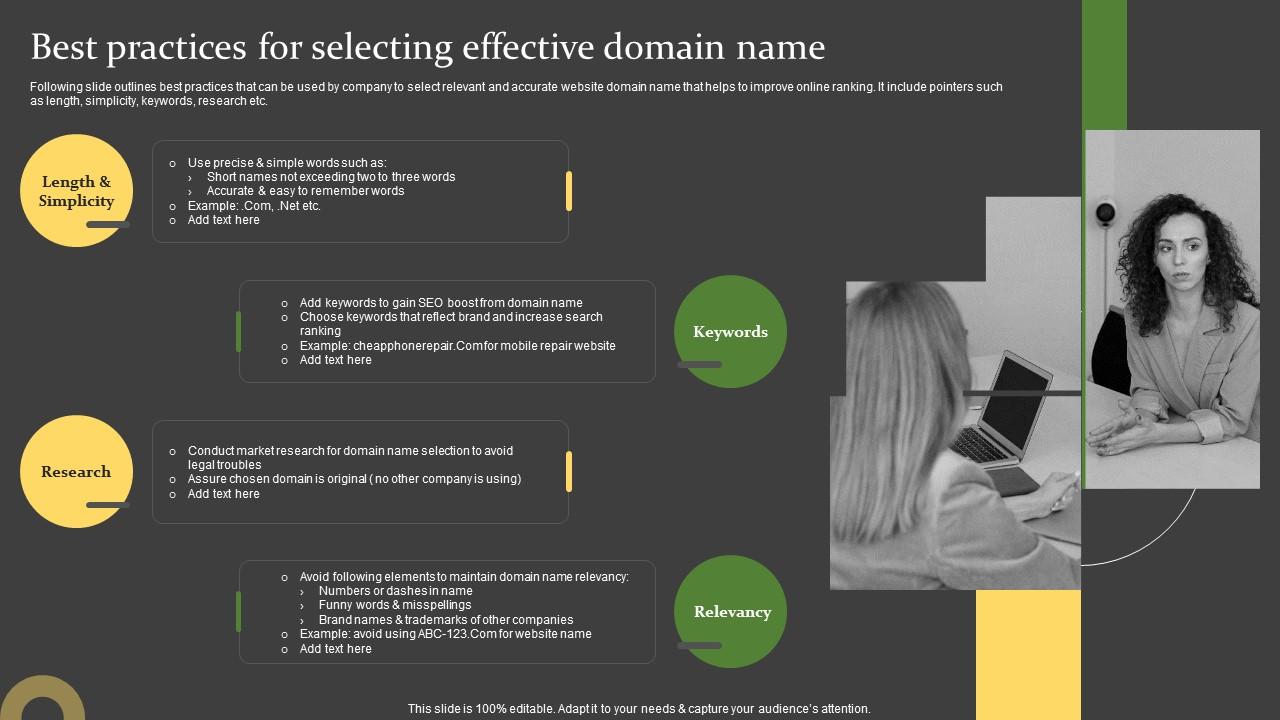
Best Practices for Selecting a Domain Name for SEO Success
Choosing a domain name for SEO involves selecting a short, memorable name that reflects your brand and includes relevant keywords. Aim for a .com extension, as it is the most recognized and trusted by users. Best Practices for Selecting a Domain Name for SEO:Selecting the right domain name is crucial for establishing an online presence.
-

How to Choose the Best Domain Name for a New Website: Insider Tips
To choose the best domain name for a new website, keep it short, memorable, and relevant to your brand. Avoid complex words and use a familiar extension like .com. How to Choose the Best Domain Name for a New Website:Selecting the right domain name is crucial for establishing an online presence. A strong domain not
