Author: Wasim Khan Sujon
-
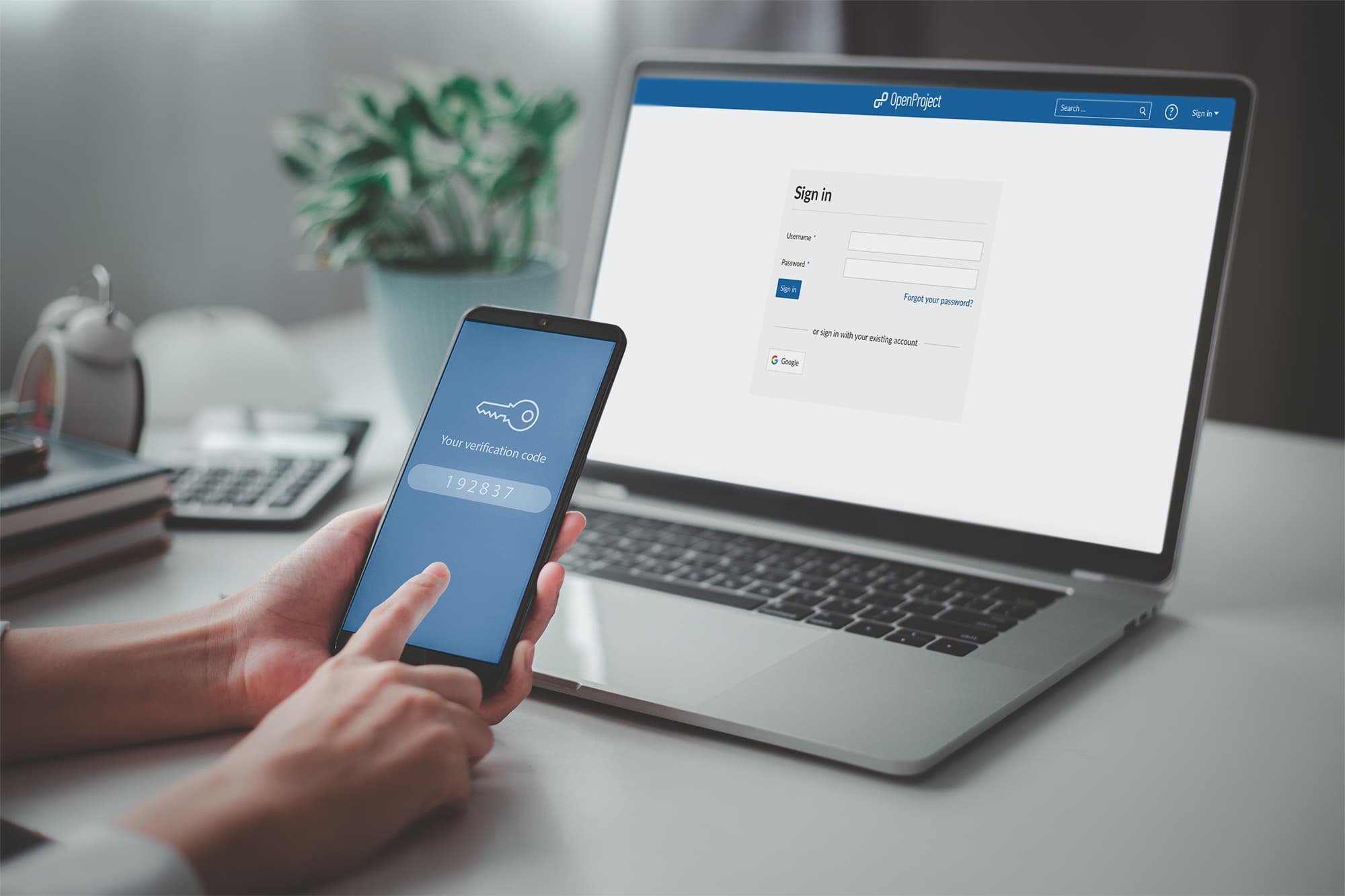
How to Implement Multi-Factor Authentication: Boost Security!
To implement multi-factor authentication (MFA) for data protection, choose an MFA solution that suits your needs. Then, enable MFA on all user accounts to enhance security. How to Implement Multi-Factor Authentication:Data protection is increasingly vital in today’s digital landscape. With cyber threats on the rise, relying solely on passwords is no longer sufficient. Multi-factor authentication
-

Role of Artificial Intelligence: Boosting InfoSec Defenses
Artificial Intelligence (AI) plays a crucial role in enhancing information security by automating threat detection and response. It analyzes vast amounts of data to identify unusual patterns and potential vulnerabilities. Role of Artificial Intelligence:The digital landscape is constantly evolving, posing new challenges for information security. Cyber threats are becoming more sophisticated, making traditional defense mechanisms
-
Steps to Secure Sensitive Data: Cloud Safety Essentials
To secure sensitive data on cloud storage platforms, use strong encryption methods and implement multi-factor authentication. Regularly review access controls and maintain updated software to protect against vulnerabilities. Steps to Secure Sensitive Data:As businesses increasingly rely on cloud storage, safeguarding sensitive data becomes crucial. Cloud platforms offer convenience and scalability, but they also pose significant
-
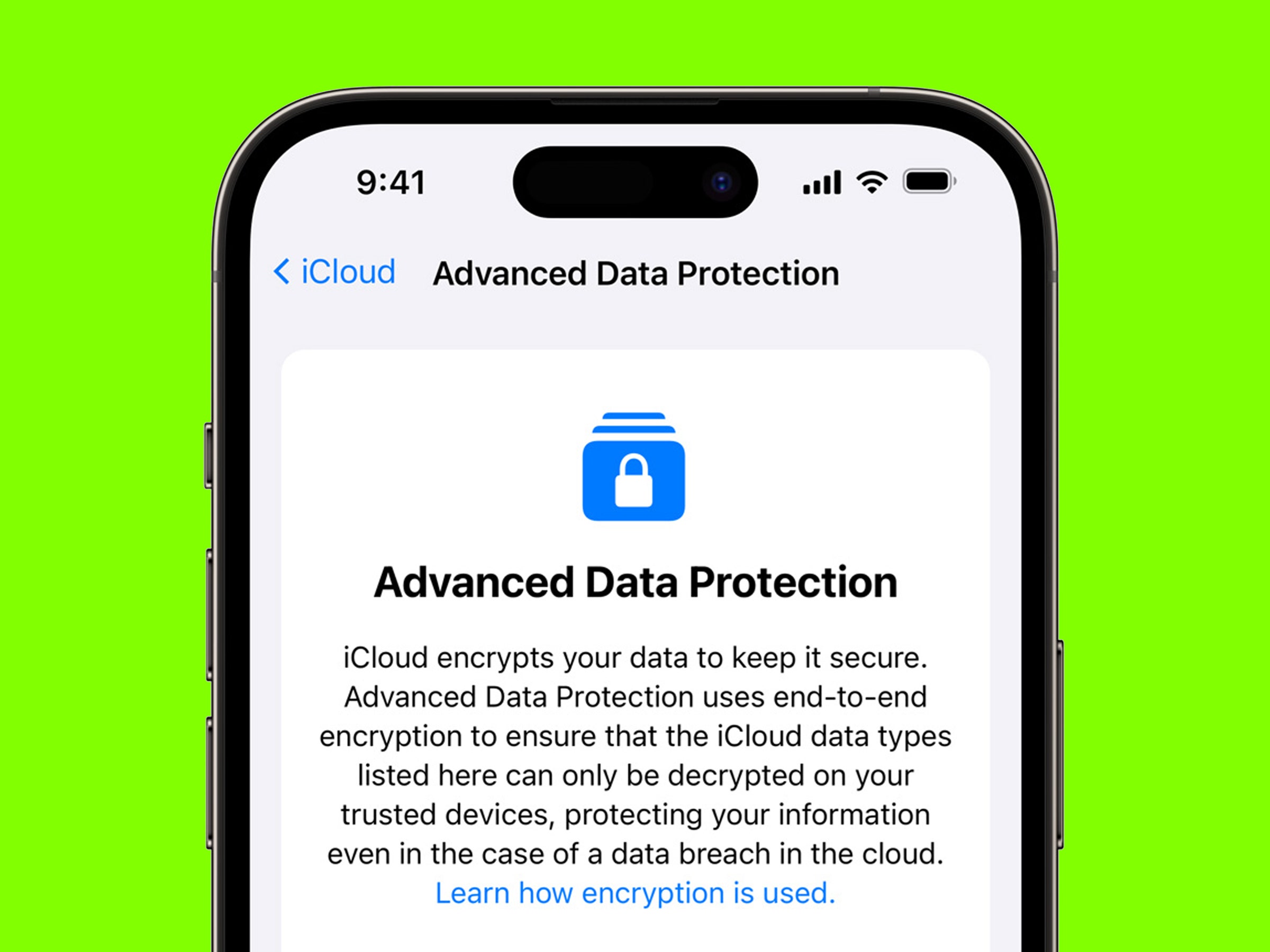
How to Secure Mobile Devices: Guard Against Data Leaks!
To secure mobile devices against information security breaches, implement strong passwords and enable biometric authentication. Regularly update software and apps to patch vulnerabilities. How to Secure Mobile Devices:Mobile devices have become essential for daily communication and business operations. With their increasing use, the risk of information security breaches also rises. Cybercriminals exploit vulnerabilities in mobile
-
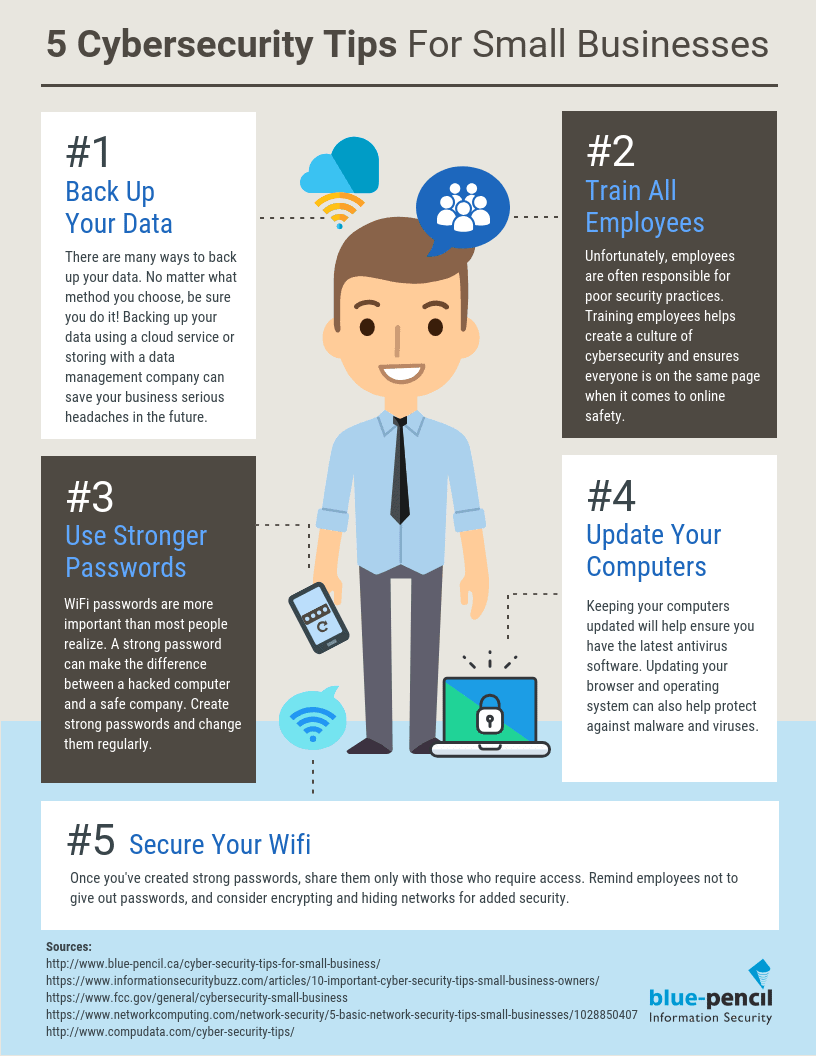
Best Practices for InfoSec in SMEs: Proven Strategies
Best practices for information security management in small businesses include implementing strong access controls and conducting regular security training for employees. Regularly updating software and creating an incident response plan are also essential. Best Practices for InfoSec in SMEs:Small businesses often face unique challenges regarding information security. Limited resources and staff can make them vulnerable
-

Understanding the Importance of Encryption: Secure Your Data!
Encryption is crucial for protecting sensitive data from unauthorized access. It ensures that information remains confidential and secure, even if intercepted. Understanding the Importance of Encryption:In today’s digital landscape, data breaches and cyber threats are rampant. Organizations and individuals alike face the risk of exposing sensitive information. Encryption plays a vital role in safeguarding this
-
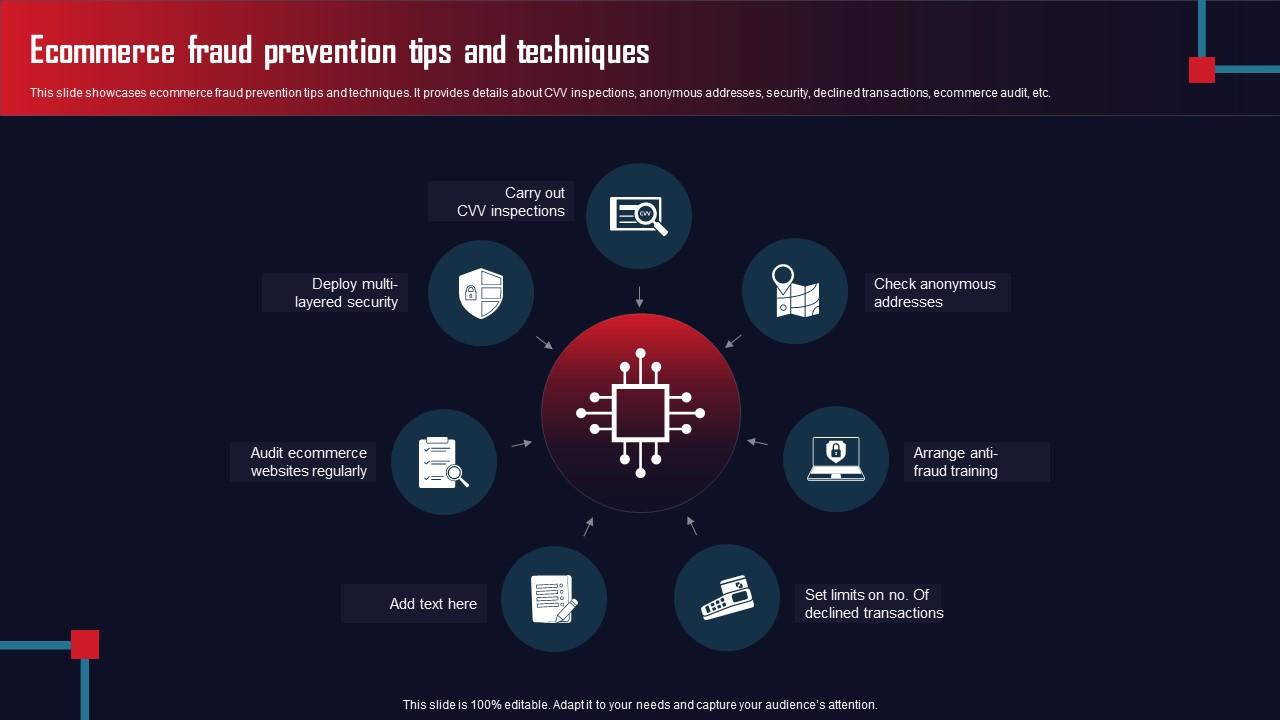
Application Security for E-Commerce: Essential Tips & Tools
Application security for e-commerce websites is crucial to protect customer data and maintain trust. Implementing robust security measures can prevent data breaches and cyberattacks. E-commerce websites handle sensitive customer information, making them prime targets for cyber threats. With the rise in online shopping, ensuring application security is more important than ever. Vulnerabilities can lead to
-

Top Application Security Testing Tools: Small Biz Essentials
Top application security testing tools for small businesses include OWASP ZAP and Veracode. These tools help identify vulnerabilities and enhance application security efficiently. Small businesses face unique challenges in application security. Limited resources and growing cyber threats make robust security essential. Application security testing tools play a crucial role in safeguarding sensitive data. They help
-
Understanding Encryption: Safeguarding Your Apps Security
Encryption plays a crucial role in application security by protecting sensitive data from unauthorized access. It ensures that even if data is intercepted, it remains unreadable without the correct decryption key. Safeguarding Your Apps Security:Encryption is a fundamental aspect of application security, ensuring that sensitive information remains confidential and secure. As cyber threats continue to
-

Guide to Application Security Compliance for Healthcare: Safeguard Essentials
Application security compliance in healthcare ensures that sensitive patient data is protected according to regulatory standards. Key frameworks include HIPAA and HITECH, which mandate strict security measures. Guide to Application Security Compliance for Healthcare:Healthcare organizations face increasing pressure to maintain application security compliance. As cyber threats grow, safeguarding patient information becomes paramount. Compliance not only
