Author: Wasim Khan Sujon
-
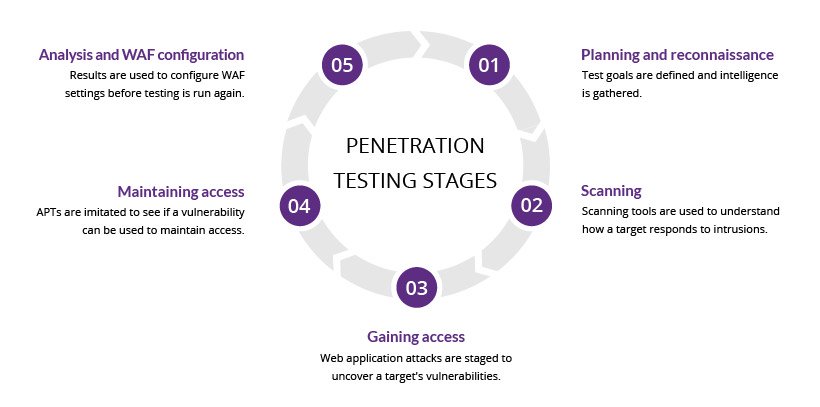
How to Conduct a Web Application Penetration Test: Essential Guide
To conduct a web application penetration test, define the scope and gather relevant information about the application. Next, use automated tools and manual techniques to identify vulnerabilities. How to Conduct a Web Application Penetration Test:Web application penetration testing is essential for identifying security weaknesses in online platforms. As cyber threats evolve, businesses must prioritize protecting
-

Importance of Penetration Testing: Cyber Defense Must-Have
Penetration testing is crucial in cybersecurity as it identifies vulnerabilities before attackers exploit them. This proactive approach helps organizations strengthen their defenses and safeguard sensitive data. Importance of Penetration Testing:Cybersecurity threats are ever-evolving, making it vital for businesses to stay one step ahead. Penetration testing simulates real-world attacks, allowing organizations to uncover weaknesses in their
-

Best Penetration Testing Tools for Beginners: Top Picks!
**Best Penetration Testing Tools for Beginners:** The top penetration testing tools for beginners include Nmap, Metasploit, and Burp Suite. These tools offer user-friendly interfaces and robust features for effective testing. Penetration testing is essential for identifying vulnerabilities in systems and networks. For beginners, selecting the right tools can significantly enhance learning and effectiveness. Nmap excels
-

Legal and Ethical Considerations in Penetration Testing: Best Practices
Penetration testing involves legal and ethical considerations that must be addressed to avoid liability. Consent from the organization and adherence to relevant laws are crucial for a successful test. Legal and Ethical Considerations in Penetration Testing:Penetration testing is essential for assessing an organization’s security posture. It identifies vulnerabilities before malicious actors can exploit them. However,
-
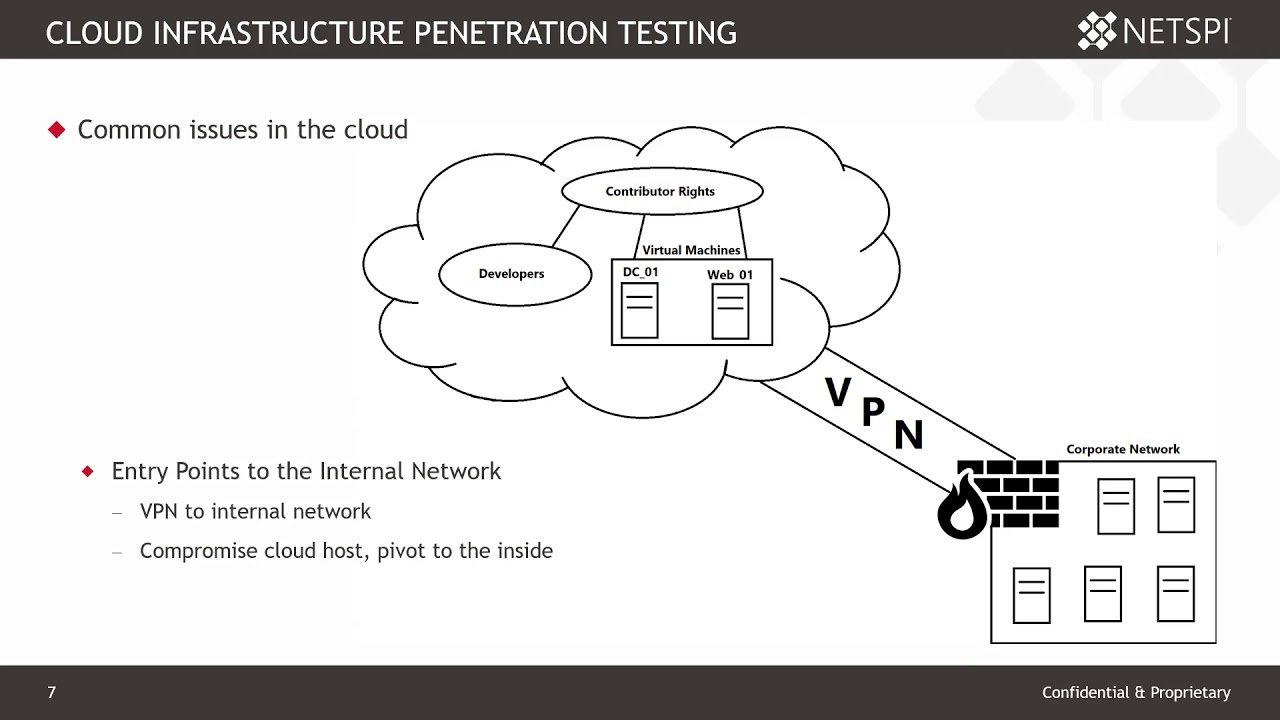
How to Perform Penetration Testing on Cloud Infrastructure: Secure It Now!
To perform penetration testing on cloud infrastructure, start by defining the scope and identifying assets. Use automated tools and manual techniques to assess vulnerabilities and risks. How to Perform Penetration Testing on Cloud Infrastructure:Penetration testing is essential for securing cloud environments. As businesses increasingly rely on cloud services, identifying weaknesses becomes critical. This proactive approach
-

Penetration Testing Best Practices for E-Commerce Websites: Secure Your Sales!
Penetration testing best practices for e-commerce websites include regular testing, thorough vulnerability assessments, and immediate remediation of identified issues. Implementing robust security measures protects customer data and enhances overall trust. E-commerce websites are prime targets for cybercriminals due to the sensitive information they handle. With increasing online transactions, ensuring security is paramount. Penetration testing simulates
-

Penetration Testing Techniques for Wireless Networks: Secure Now!
Penetration testing techniques for wireless networks include signal interception, rogue access point deployment, and packet sniffing. These methods help identify vulnerabilities in network security. Wireless networks are essential for modern connectivity, but they also pose unique security challenges. Penetration testing plays a crucial role in safeguarding these networks from potential threats. By simulating cyber-attacks, security
-

Step-By-Step Guide to Network Penetration Testing: Secure Your System!
Network penetration testing involves simulating cyber attacks to identify vulnerabilities in a system. This step-by-step guide outlines methods to enhance network security effectively. Step-By-Step Guide to Network Penetration Testing:Penetration testing is crucial for safeguarding sensitive data and maintaining system integrity. Organizations face increasing threats from cybercriminals, making proactive security measures essential. This guide simplifies the
-
Penetration Testing Methodologies for Small Businesses: Secure Now!
Penetration testing methodologies for small businesses include black-box, white-box, and gray-box testing. Each approach helps identify vulnerabilities based on different levels of information access. Cybersecurity remains a top priority for small businesses facing increasing digital threats. Understanding penetration testing methodologies is essential for safeguarding sensitive data. Black-box testing simulates an external attack with no prior
-

Top Certifications for Penetration Testing Pros: Master Cybersecurity!
Top certifications for penetration testing professionals include Certified Ethical Hacker (CEH) and Offensive Security Certified Professional (OSCP). These credentials enhance skills and marketability in cybersecurity. Top Certifications for Penetration Testing Pros:Penetration testing is crucial in identifying vulnerabilities in systems and networks. As cyber threats grow, professionals must equip themselves with relevant skills and certifications. Various
