Author: Wasim Khan Sujon
-

The Role of Artificial Intelligence in Cybersecurity: Shielding Data
Artificial Intelligence (AI) enhances cybersecurity by automating threat detection and response. It analyzes vast data sets to identify patterns and anomalies quickly. The Role of Artificial Intelligence in Cybersecurity:As digital threats grow in complexity, organizations increasingly rely on AI to bolster their cybersecurity measures. Traditional methods struggle to keep pace with evolving threats, making AI
-

Guide to Choosing a Cybersecurity Solution for Your Company: Smart Tips
Choosing the right cybersecurity solution involves assessing your company’s specific needs and evaluating available options. Focus on scalability, ease of use, and compliance with industry regulations. Guide to Choosing a Cybersecurity Solution for Your Company:Cybersecurity is essential for protecting your company’s sensitive data and maintaining trust with customers. With increasing cyber threats, selecting an effective
-

How to Secure Your Home Network: Defend Against Cyber Threats
To secure your home network from cyber attacks, use strong, unique passwords for your devices. Regularly update your router’s firmware and enable network encryption. How to Secure Your Home Network:As our lives become increasingly connected, protecting your home network is essential. Cyber attacks can lead to data theft, privacy breaches, and financial loss. A secure
-
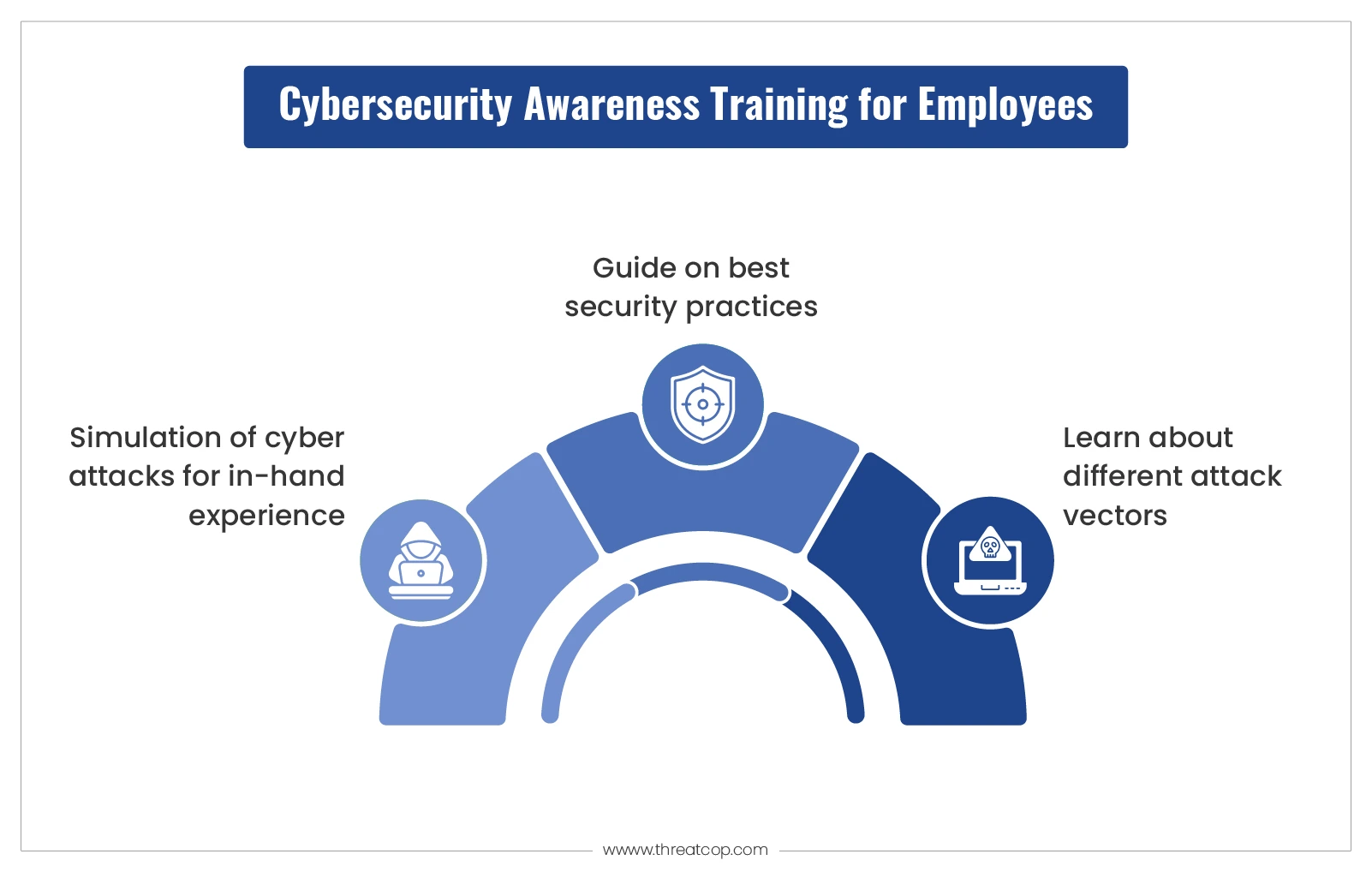
Cybersecurity Awareness Training for Employees: Enhance Vigilance!
Cybersecurity awareness training for employees educates them about potential threats and safe online behaviors. This training is crucial for protecting sensitive data and maintaining organizational integrity. Cybersecurity threats are ever-evolving, making employee training vital for any organization. Employees often serve as the first line of defense against cyberattacks. By understanding common threats like phishing, malware,
-

Best Cybersecurity Strategies for Small Businesses: Top Tips!
The best cybersecurity strategies for small businesses include implementing strong password policies and regularly updating software. Training employees on security best practices is essential for minimizing risks. Cybersecurity is crucial for small businesses, often targeted by cybercriminals due to limited resources. Many small enterprises lack robust security measures, making them vulnerable to attacks. With the
-
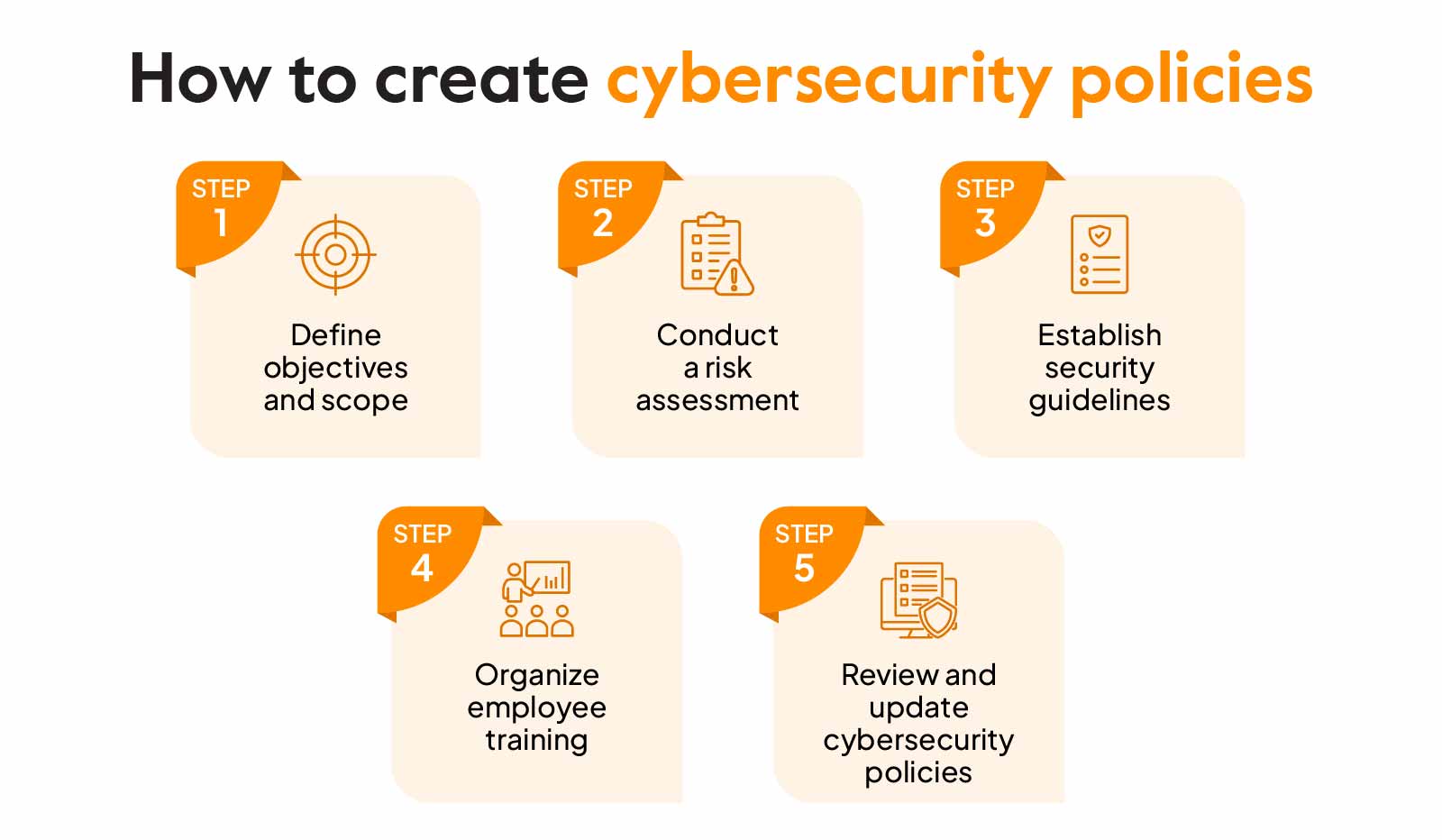
How to Create an Effective Cybersecurity Policy: 5 Key Steps
To create an effective cybersecurity policy, identify key assets and assess potential threats. Develop clear guidelines that outline acceptable use, access controls, and incident response protocols. How to Create an Effective Cybersecurity Policy:Cybersecurity is crucial for protecting sensitive information and maintaining trust. A well-crafted policy safeguards your organization against threats and establishes a security framework.
-
Preventing Data Breaches in Cloud Computing Environments: Pro Tips
To prevent data breaches in cloud computing environments, implement strong encryption and regular security audits. User access controls and employee training are also essential. Preventing Data Breaches in Cloud Computing Environments:Cloud computing offers significant advantages, but it also presents unique security challenges. Data breaches can lead to severe consequences, including financial loss and reputational damage.
-

How to Secure Remote Access for Employees: Smart Tips
To secure remote access for employees, implement a Virtual Private Network (VPN) and enforce strong password policies. Regularly update security protocols and provide employee training on safe practices. How to Secure Remote Access for Employees:In today’s digital workplace, remote access has become essential. Companies must prioritize security to protect sensitive information and maintain productivity. With
-
How to Implement Multi-Factor Authentication: Secure Your Office Now!
To implement multi-factor authentication (MFA) in the workplace, choose an MFA provider that suits your needs. Next, educate employees on the importance and process of using MFA. How to Implement Multi-Factor Authentication:Multi-factor authentication is essential for enhancing workplace security. Cyber threats are on the rise, making traditional passwords insufficient. MFA adds an extra layer of
-

The Role of Encryption: Your Shield for Data Privacy
Encryption plays a crucial role in protecting sensitive data by converting it into an unreadable format. This process ensures that only authorized users can access the information. The Role of Encryption:Sensitive data, such as personal information and financial records, is vulnerable to unauthorized access and cyber threats. Encryption serves as a robust defense mechanism, safeguarding
