Author: Wasim Khan Sujon
-

How to Get Started With Ethical Hacking in 2024: A Beginner’s Guide
To get started with ethical hacking in 2024, learn the basics of networking and programming. Obtain relevant certifications like CEH or OSCP. How to Get Started With Ethical Hacking in 2024:Ethical hacking, also known as penetration testing, involves legally probing systems for vulnerabilities. Begin by understanding fundamental concepts in networking, such as TCP/IP, DNS, and
-

Cybersecurity Tools for Small Businesses: Top Picks & Tips
Small businesses can enhance their cybersecurity by using tools like firewalls, antivirus software, and data encryption. Regular software updates and employee training are also crucial. Cybersecurity Tools for Small Businesses:Cybersecurity is a pressing concern for small businesses, as they often lack the resources to combat cyber threats. Many small companies mistakenly believe they are too
-

What is a Cybersecurity Risk Assessment?: Unveil Threats
A Cybersecurity Risk Assessment evaluates potential threats to an organization’s information systems. It identifies vulnerabilities and assesses their impact on data security. What is a Cybersecurity Risk Assessment:Cybersecurity is a growing concern for businesses of all sizes. Organizations face numerous threats, including data breaches, malware, and insider threats. A Cybersecurity Risk Assessment is crucial in
-

Cybersecurity Measures for Remote Workers: Stay Safe Online
Implementing strong cybersecurity measures for remote workers is crucial. Key strategies include using VPNs, secure passwords, and regular software updates. The rise of remote work has transformed the business landscape, making cybersecurity more vital than ever. As employees access sensitive data from home, they become prime targets for cybercriminals. Companies must prioritize cybersecurity to protect
-

How to Secure Your Wi-Fi Network at Home: Top Tips!
To secure your Wi-Fi network at home, change the default password and enable WPA3 encryption. Regularly update your router’s firmware for optimal security. How to Secure Your Wi-Fi Network at Home:In today’s digital age, a secure Wi-Fi network is essential for protecting your personal information. With more devices connecting to the internet than ever, vulnerabilities
-
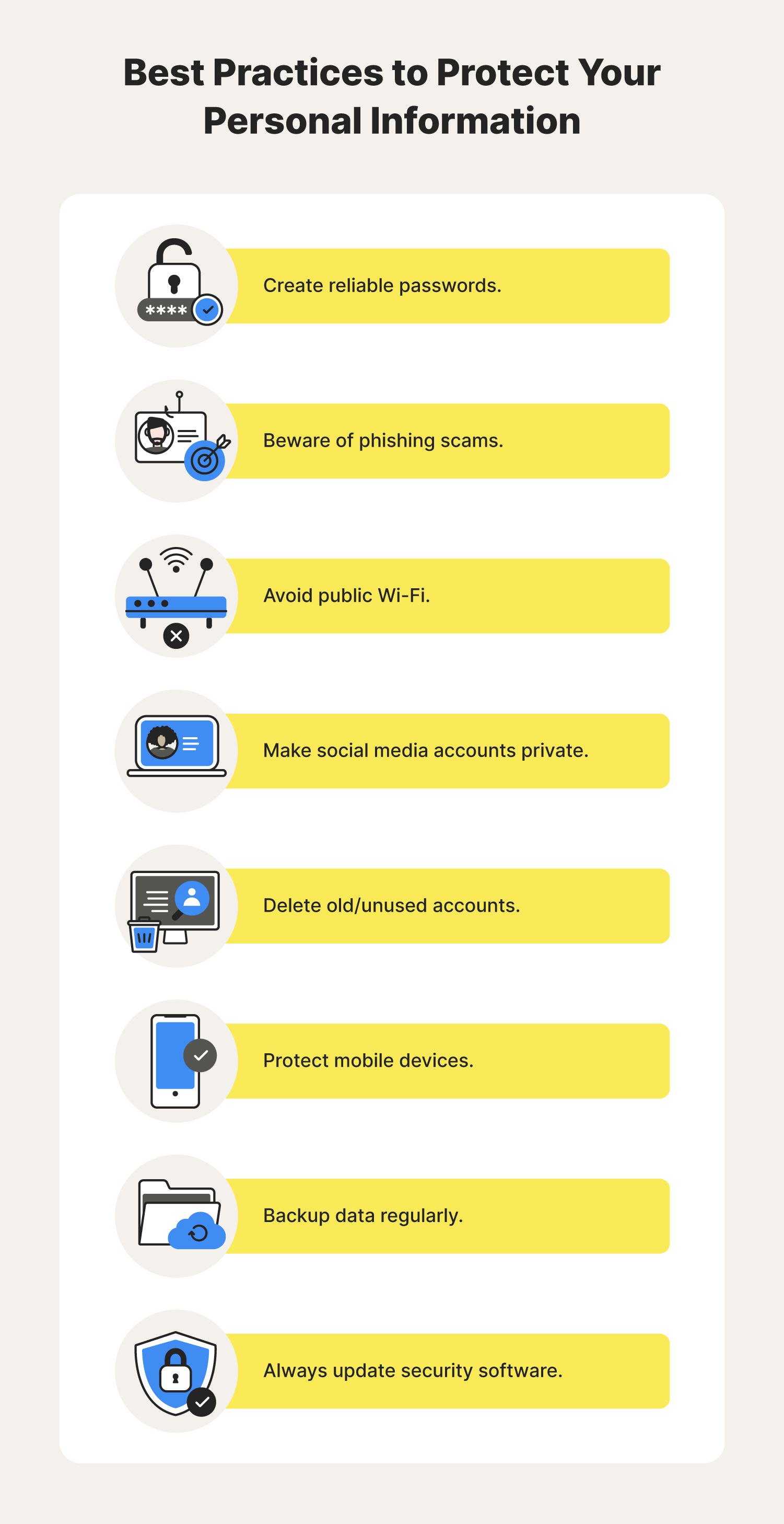
How to Protect Personal Data Online: Safeguard Secrets!
To protect personal data online, use strong, unique passwords and enable two-factor authentication. Regularly update your software and be cautious with public Wi-Fi. How to Protect Personal Data Online:In today’s digital landscape, safeguarding personal data is more crucial than ever. Cyber threats, such as identity theft and data breaches, can have severe consequences. With increasing
-

Best Tools for Penetration Testing in 2024: Unleash Security
**Best Tools for Penetration Testing in 2024:** Top tools include Metasploit, Burp Suite, and Nmap. These tools provide comprehensive features for effective testing. Penetration testing is essential for identifying security vulnerabilities in systems and networks. As cyber threats evolve, so do the tools used for testing. In 2024, various tools stand out for their effectiveness
-

How to Choose the Right Penetration Testing Service: Expert Tips
To choose the right penetration testing service provider, assess their certifications and experience in the industry. Evaluate their methodologies and tools to ensure they align with your specific security needs. How to Choose the Right Penetration Testing Service:Selecting a penetration testing service provider is crucial for safeguarding your organization’s sensitive data. Cyber threats continue to
-

Penetration Testing for SMBs: Unlock Ultimate Security!
Penetration testing for small businesses identifies security vulnerabilities by simulating cyber attacks. This process helps strengthen defenses and protects sensitive data. Penetration Testing for SMBs:Small businesses face unique cybersecurity challenges. Limited resources and lack of expertise make them attractive targets for cybercriminals. Penetration testing serves as a proactive measure to uncover vulnerabilities before malicious actors
-

Best Penetration Testing Tools for Ethical Hackers: Top Picks
Top penetration testing tools for ethical hackers include Metasploit, Nmap, and Burp Suite. These tools enhance security assessments by identifying vulnerabilities effectively. Best Penetration Testing Tools for Ethical Hackers:Penetration testing plays a crucial role in cybersecurity. Ethical hackers use specialized tools to simulate attacks and uncover weaknesses in systems. By leveraging these tools, professionals can
