Encryption plays a crucial role in application security by protecting sensitive data from unauthorized access. It ensures that even if data is intercepted, it remains unreadable without the correct decryption key.
Safeguarding Your Apps Security:Encryption is a fundamental aspect of application security, ensuring that sensitive information remains confidential and secure. As cyber threats continue to evolve, protecting data in transit and at rest is more important than ever. By converting information into a coded format, encryption prevents unauthorized users from accessing critical data.
This technology safeguards personal details, financial records, and intellectual property. Organizations must implement robust encryption protocols to comply with regulations and maintain customer trust. Understanding the nuances of encryption helps developers and businesses build more secure applications, ultimately enhancing overall cybersecurity measures. Emphasizing encryption is essential in today’s digital landscape.
Credit: www.softwareseni.com
The Essence Of Encryption In Modern Apps
Encryption plays a vital role in modern applications. It protects sensitive data from unauthorized access. With increasing cyber threats, encryption ensures user trust and data integrity. Understanding its importance helps developers enhance application security.
Protecting Data At Rest
Data at rest refers to inactive data stored physically. This includes files on servers, databases, and devices. Protecting this data is crucial for security. Encryption safeguards it against breaches and theft.
- Encryption Algorithms: Common algorithms include AES and RSA.
- Data Encryption Standards: Use FIPS 140-2 for compliance.
- Access Controls: Limit who can access encrypted data.
Implementing encryption for data at rest involves:
- Choosing the right encryption method.
- Storing encryption keys securely.
- Regularly updating encryption protocols.
Securing Data In Transit
Data in transit refers to data moving across networks. This includes emails, file transfers, and API calls. Securing this data is essential to prevent interception.
| Method | Description |
|---|---|
| SSL/TLS | Secures data between browsers and servers. |
| VPN | Encrypts data over public networks. |
| SSH | Securely accesses remote servers. |
For effective protection during transit:
- Implement SSL/TLS for web applications.
- Use VPNs for secure remote access.
- Adopt secure protocols for data exchange.
Types Of Encryption Techniques
Encryption is vital for application security. It protects sensitive data from unauthorized access. Different techniques exist to ensure data safety. Understanding these methods helps in selecting the right one.
Symmetric Vs. Asymmetric Encryption
Encryption techniques can be categorized into two main types: symmetric and asymmetric.
| Feature | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Key Usage | Same key for encryption and decryption | Two keys: public and private |
| Speed | Faster | Slower |
| Use Case | Large data encryption | Secure key exchange |
| Examples | AES, DES | RSA, ECC |
Symmetric encryption uses one key. This key encrypts and decrypts data. It’s fast and efficient for large amounts of data.
Asymmetric encryption involves two keys. One is public, while the other is private. This method allows for secure communication over the internet.
Hashing For Data Integrity
Hashing is a technique used for data integrity. It converts data into a fixed-length string. This string represents the original data.
- Key Features of Hashing:
- Irreversible: Cannot convert back to original data.
- Unique: Small changes in data produce different hashes.
- Fast: Quick to compute and verify.
Common hashing algorithms include:
- MD5
- SHA-1
- SHA-256
Hashing ensures that data remains unchanged. It’s crucial for verifying the integrity of files and messages.
Implementing Encryption In App Development
Encryption is crucial in app development. It protects sensitive data from unauthorized access. Proper implementation ensures user trust and data integrity.
Choosing The Right Encryption Algorithm
Selecting the right encryption algorithm is essential. Different algorithms serve various purposes. Here are some popular options:
- AES (Advanced Encryption Standard): Strong and widely used.
- RSA (Rivest–Shamir–Adleman): Suitable for secure key exchange.
- ChaCha20: Fast and secure for mobile devices.
Consider these factors:
- Security Level: Assess the strength of each algorithm.
- Performance: Ensure it runs efficiently on your platform.
- Compliance: Follow industry regulations and standards.
Best Practices For Key Management
Key management is vital for encryption success. Poor practices can lead to data breaches. Follow these best practices:
| Practice | Description |
|---|---|
| Use Strong Keys | Generate complex keys to enhance security. |
| Rotate Keys Regularly | Change keys frequently to minimize risk. |
| Store Keys Securely | Use secure vaults to protect keys. |
| Limit Access | Grant access to only necessary personnel. |
Implementing these practices enhances the security of your application. Protect user data effectively.
The Role Of Ssl/tls In App Security
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are vital for app security. They protect data during transmission. These protocols encrypt information, making it unreadable to hackers. Using SSL/TLS ensures secure connections for users. This enhances trust in applications.
How Ssl/tls Works
SSL/TLS operates through a series of steps:
- Connection Establishment: A secure connection starts with a handshake.
- Authentication: The server provides a digital certificate.
- Session Keys: Both parties create unique session keys.
- Data Encryption: Information is encrypted during transmission.
- Data Integrity: Checks ensure data hasn’t changed.
This process ensures that only authorized users access sensitive information.
Ssl/tls Implementation Challenges
Implementing SSL/TLS comes with challenges:
- Certificate Management: Keeping certificates up to date is crucial.
- Performance Issues: Encryption can slow down applications.
- Misconfigurations: Incorrect setup can lead to vulnerabilities.
- Cost: Obtaining certificates may incur expenses.
Addressing these challenges is key for secure application environments.
| Challenge | Impact | Solution |
|---|---|---|
| Certificate Management | Expired certificates can cause downtime. | Automate renewal processes. |
| Performance Issues | Slow load times frustrate users. | Optimize server resources. |
| Misconfigurations | Security holes may expose data. | Regular audits and testing. |
| Cost | Budget constraints limit security measures. | Consider free certificate options. |
Common Encryption Standards And Protocols
Understanding encryption standards and protocols is crucial. They protect data from unauthorized access. Many applications use these methods to ensure security.
Aes And Rsa In The Spotlight
AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) are popular encryption methods.
- AES:
- Symmetric key encryption.
- Uses the same key for encryption and decryption.
- Fast and efficient.
- RSA:
- Asymmetric key encryption.
- Uses a public key for encryption and a private key for decryption.
- Slower but highly secure.
| Standard | Type | Key Usage | Speed |
|---|---|---|---|
| AES | Symmetric | Same key | Fast |
| RSA | Asymmetric | Public/Private keys | Slower |
Understanding Ssl, Tls, And Https
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are essential for secure communication.
- SSL: Older protocol for securing data.
- TLS: Improved version of SSL. Offers better security.
HTTPS (HyperText Transfer Protocol Secure) uses SSL/TLS to encrypt data between your browser and the server.
Key benefits of HTTPS include:
- Data protection during transmission.
- Improved user trust.
- Better SEO rankings.
Websites with HTTPS show a padlock icon. This indicates a secure connection.
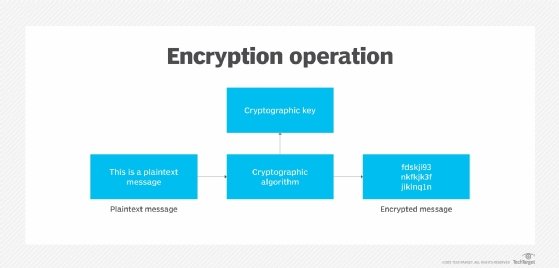
Credit: www.techtarget.com
Performance Implications Of Encryption
Encryption is vital for securing applications. It protects sensitive data from unauthorized access. However, it can affect application performance. Understanding this balance is crucial for developers.
Performance implications include increased processing time and resource usage. This section explores how to manage these factors effectively.
Balancing Security And Speed
Finding the right balance between security and speed is essential. Applications must protect data while maintaining performance. Here are key factors to consider:
- Type of encryption: Different methods have varying speeds.
- Data size: Larger data takes more time to encrypt.
- Hardware capabilities: Stronger hardware can speed up processes.
Developers must evaluate these factors. Prioritize what matters most for the application. Security should not compromise usability.
Optimizing Encryption For Performance
Optimizing encryption can enhance performance. Here are effective strategies:
- Choose efficient algorithms: Use algorithms that provide strong security with low overhead.
- Implement hardware acceleration: Leverage dedicated hardware for faster encryption.
- Minimize encryption calls: Reduce the frequency of encryption operations to save time.
- Use caching: Cache encrypted data to avoid repeated encryption.
Table 1 shows the performance impact of various encryption algorithms.
| Algorithm | Security Level | Speed (MB/s) |
|---|---|---|
| AES | High | 1200 |
| RSA | Very High | 50 |
| ChaCha20 | High | 1000 |
Selecting the right algorithm can significantly improve performance. Make informed choices to enhance both security and speed.
Legal And Compliance Aspects Of Encryption
Understanding the legal and compliance aspects of encryption is crucial. Organizations must follow laws and regulations. These rules protect data and ensure users’ privacy. Failure to comply can lead to heavy fines. Proper encryption strategies help meet these legal requirements.
Navigating Gdpr And Other Regulations
The General Data Protection Regulation (GDPR) is one of the strictest laws. It applies to all businesses that handle data of EU citizens. Here are key points regarding GDPR and encryption:
- Data Protection: GDPR mandates protecting personal data.
- Encryption: Encrypting data can help meet compliance.
- Data Breach Notification: Businesses must notify users of breaches.
- Privacy by Design: Encryption should be built into systems.
Other regulations, like HIPAA and PCI DSS, also emphasize encryption. These laws safeguard health and financial information.
Encryption Export Controls And Restrictions
Encryption software is subject to export controls. Different countries have various rules. Organizations must understand these restrictions. Here’s an overview:
| Country | Encryption Export Rules |
|---|---|
| United States | Requires licenses for strong encryption export. |
| European Union | Less strict; some restrictions apply. |
| China | Strict controls; requires government approval. |
Organizations must stay updated on these laws. Non-compliance can lead to penalties. Always consult legal experts when implementing encryption.

Credit: www.simplilearn.com
Future Of Encryption Technology
The future of encryption technology is bright and full of possibilities. As digital threats grow, encryption will evolve. This evolution will secure data better than ever.
Quantum Computing And Encryption
Quantum computing poses new challenges for encryption. Traditional encryption methods may become vulnerable. Quantum computers can solve complex problems quickly.
Here are key points about quantum computing and encryption:
- Speed: Quantum computers can break current encryption in seconds.
- Security: New algorithms are needed for protection.
- Post-Quantum Cryptography: Researchers are developing stronger encryption methods.
Organizations must prepare for quantum threats. Adopting post-quantum cryptography is essential. This will ensure data remains safe.
Emerging Trends In Cryptography
Many new trends are shaping the future of cryptography. These trends focus on better security and usability.
| Trend | Description |
|---|---|
| Homomorphic Encryption | Allows computations on encrypted data without decryption. |
| Blockchain Technology | Enhances data integrity and transparency in transactions. |
| Zero-Knowledge Proofs | Proves information without revealing the data itself. |
These trends will change how we protect data. They will also improve user experience. Businesses must adapt to these changes.
Investing in new encryption methods is crucial. This helps secure sensitive information. Staying ahead will ensure safety in a digital world.
Frequently Asked Questions
What Is Encryption In Application Security?
Encryption in application security is the process of converting data into a coded format. This ensures that unauthorized users cannot access or understand sensitive information. It plays a crucial role in protecting data integrity and confidentiality, thereby enhancing overall application security.
Why Is Encryption Important For Data Protection?
Encryption is vital for data protection as it safeguards sensitive information from unauthorized access. It protects user data during transmission and storage, reducing the risk of data breaches. By ensuring that only authorized individuals can read the data, encryption boosts user trust and compliance with regulations.
How Does Encryption Prevent Data Breaches?
Encryption prevents data breaches by making stolen data unreadable. Even if cybercriminals gain access to encrypted information, they cannot decipher it without the decryption key. This adds a significant layer of security, making it more challenging for attackers to exploit sensitive data.
What Types Of Encryption Are Commonly Used?
Common types of encryption include symmetric and asymmetric encryption. Symmetric encryption uses the same key for both encryption and decryption. Asymmetric encryption uses a pair of keys: a public key for encryption and a private key for decryption. Each type serves different security needs.
Conclusion
Encryption is essential for securing applications against data breaches and unauthorized access. It protects sensitive information by converting it into unreadable code. Implementing robust encryption strategies enhances user trust and compliance with regulations. Prioritizing encryption in your application security strategy will safeguard your data and maintain your reputation in the digital landscape.



Leave a Reply