Ethical hacking involves authorized testing to find security vulnerabilities. Black hat hacking exploits these vulnerabilities for malicious purposes.
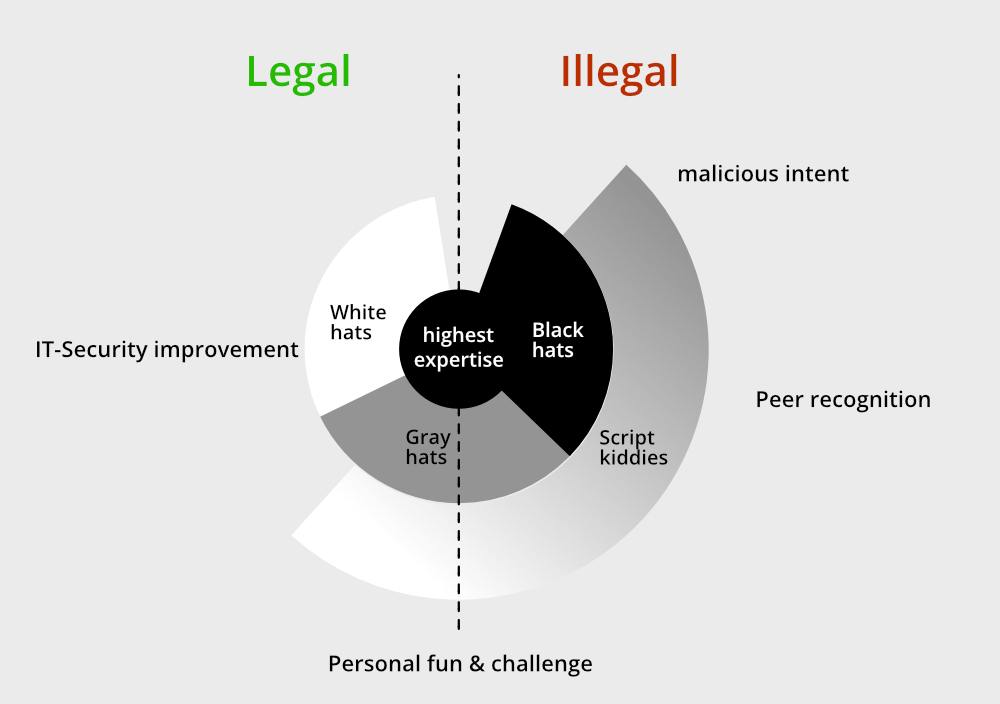
Ethical Hacking Vs. Black Hat Hacking:Ethical hacking and black hat hacking represent two sides of the cybersecurity spectrum. Ethical hackers, also known as white hat hackers, help organizations by identifying and fixing security flaws. They work legally and ensure data protection. Black hat hackers, on the other hand, engage in illegal activities for personal gain, causing harm to individuals and businesses.
Understanding the differences between these two practices is crucial for maintaining cybersecurity. Ethical hackers play a vital role in safeguarding information, while black hat hackers pose significant threats. By distinguishing these roles, we can better appreciate the importance of ethical hacking in today’s digital world.
Core Objectives
The core objectives of ethical hacking and black hat hacking differ greatly. Understanding these differences is crucial. This section will explore their intent, purpose, and legal implications.
Intent And Purpose
Ethical hacking aims to protect systems and data. Ethical hackers, or white hat hackers, identify vulnerabilities. They help companies fix these issues to enhance security. Their work is authorized and beneficial.
Black hat hacking has malicious intentions. Black hat hackers seek to exploit vulnerabilities. They aim to steal data, disrupt services, or cause harm. Their actions are illegal and unethical.
| Aspect | Ethical Hacking | Black Hat Hacking |
|---|---|---|
| Intent | Protect systems | Exploit systems |
| Purpose | Identify and fix vulnerabilities | Steal data, cause harm |
Legal Implications
Ethical hacking is legal and supported by laws. Ethical hackers work with permission. They follow a code of conduct and industry standards. Their work is vital for cybersecurity.
Black hat hacking is illegal and punishable by law. Black hat hackers face severe consequences. Legal actions include fines and imprisonment. Their activities harm individuals and organizations.
- Ethical hacking: Legal, authorized, and regulated.
- Black hat hacking: Illegal, unauthorized, and punishable.
Methods And Techniques
Understanding the methods and techniques used in ethical hacking versus black hat hacking is crucial. These approaches differ greatly in their tools, objectives, and legal implications. Here, we explore the various tools and techniques employed by ethical hackers and black hat hackers.
Ethical Hacking Tools
Ethical hackers use various tools to find vulnerabilities and secure systems. These tools help them identify, analyze, and fix security issues without causing harm.
- Nmap: A network scanning tool to discover hosts and services.
- Wireshark: A packet analyzer tool for network troubleshooting and analysis.
- Metasploit: A framework for developing and executing exploit code against a remote target.
- Burp Suite: A comprehensive platform for web application security testing.
- John the Ripper: A password cracking tool used to test password strength.
Black Hat Hacking Tools
Black hat hackers use malicious tools to exploit vulnerabilities and gain unauthorized access. These tools often cause damage, steal data, or disrupt services.
- Malware: Software designed to damage or disrupt systems.
- Keyloggers: Tools that record keystrokes to steal information.
- Botnets: Networks of infected devices used to launch attacks.
- Rootkits: Software that provides unauthorized access to a computer system.
- Phishing Kits: Tools used to create fake websites to steal credentials.
The table below summarizes the key differences between ethical hacking and black hat hacking tools:
| Tool Category | Ethical Hacking Tools | Black Hat Hacking Tools |
|---|---|---|
| Network Scanning | Nmap | Botnets |
| Packet Analysis | Wireshark | Malware |
| Exploitation | Metasploit | Rootkits |
| Web Security | Burp Suite | Phishing Kits |
| Password Cracking | John the Ripper | Keyloggers |
Motivations
Understanding the motivations behind ethical hacking and black hat hacking is crucial. These motivations drive hackers and define their actions. Let’s delve into the contrasting motivations behind these two types of hacking.
Ethical Motivations
Ethical hackers, also known as white hat hackers, aim to protect. Their primary goal is to improve security systems. They work to identify and fix vulnerabilities. Organizations hire them to safeguard their networks.
Here are some common ethical motivations:
- Protecting sensitive data from cybercriminals
- Enhancing security measures to prevent breaches
- Helping organizations comply with regulations
- Educating others about cybersecurity best practices
Malicious Motivations
Black hat hackers have harmful intentions. They exploit weaknesses for personal gain. Their actions can cause serious damage to individuals and organizations.
Common malicious motivations include:
- Financial gain through fraud or theft
- Disrupting services to cause chaos
- Stealing sensitive information for resale
- Gaining unauthorized access to confidential data
Let’s compare the motivations of both types of hackers:
| Ethical Hackers | Black Hat Hackers |
|---|---|
| Protect data | Steal data |
| Improve security | Exploit vulnerabilities |
| Follow regulations | Break laws |
| Educate others | Cause harm |

Credit: nandbox.com
Skill Sets
Understanding the skill sets of ethical hackers and black hat hackers helps in distinguishing their roles. Both require knowledge but apply it differently. This section explores their unique skills.
Required Skills For Ethical Hackers
- Networking Skills: Ethical hackers must understand network protocols.
- Programming Knowledge: Familiarity with languages like Python, C++, Java.
- Operating Systems: Proficiency in Windows, Linux, and Unix.
- Cryptography: Knowledge of encryption and decryption methods.
- Problem-Solving: Ability to identify and fix security issues.
Skills Black Hat Hackers Possess
- Advanced Coding: Expertise in writing malicious code.
- Social Engineering: Manipulating people to gain confidential information.
- Exploit Development: Creating and using software to exploit systems.
- Network Intrusion: Skills to bypass network security.
- Steganography: Hiding information within files.
| Skill | Ethical Hackers | Black Hat Hackers |
|---|---|---|
| Networking | Yes | Yes |
| Programming | Yes | Yes |
| OS Knowledge | Yes | Yes |
| Cryptography | Yes | Maybe |
| Social Engineering | No | Yes |
Impact On Society
The debate between ethical hacking and black hat hacking centers on their impact on society. Ethical hackers protect systems and data, while black hat hackers exploit them. Understanding their societal impact is crucial.
Positive Contributions
Ethical hacking offers many benefits to society. These hackers find vulnerabilities in systems. They help companies fix these flaws before black hat hackers exploit them. This protection keeps our data safe.
- Improved Security: Ethical hackers improve overall cybersecurity.
- Trust: They build trust between users and technology.
- Education: They educate others about safe online practices.
Ethical hackers also contribute to law enforcement. They help catch black hat hackers. They provide evidence in cybercrime cases. This makes the digital world safer for everyone.
Negative Consequences
Black hat hacking has many negative effects on society. These hackers steal personal information and money. They disrupt businesses and services.
- Data Breaches: Black hat hackers cause data breaches.
- Financial Loss: Companies lose money due to hacking.
- Trust Issues: Users lose trust in digital services.
Black hat hacking also has broader societal impacts. It creates fear and uncertainty. People feel unsafe online. This can hinder technology adoption and progress.
| Aspect | Ethical Hacking | Black Hat Hacking |
|---|---|---|
| Security | Improves system security | Compromises system security |
| Trust | Builds user trust | Destroys user trust |
| Impact | Positive societal impact | Negative societal impact |
Understanding these impacts helps us appreciate the value of ethical hacking. It also highlights the dangers of black hat hacking. We must support ethical practices to create a safer digital world.
Case Studies
Understanding the real-world impact of hacking requires examining case studies. These examples highlight the differences between ethical hacking and black hat hacking. This section explores notable instances of both, underlining the importance of ethical practices.
Successful Ethical Hacking
Ethical hackers strive to protect systems. They find vulnerabilities before malicious hackers do. Here’s a notable case:
| Case | Details |
|---|---|
| Google Vulnerability Reward Program | Google offers rewards for discovering bugs. Ethical hackers found critical flaws. This prevented potential large-scale breaches. |
| Facebook Bug Bounty | Facebook pays for security flaws. Hackers reported serious issues. This enhanced user safety and trust. |
Notorious Black Hat Incidents
Black hat hackers exploit systems for malicious gain. Their actions cause significant harm. Below are some notorious examples:
- Yahoo Data Breach: Hackers stole data from 3 billion accounts. Personal information was compromised.
- Equifax Hack: Sensitive data of 147 million people was exposed. This included Social Security numbers.
- WannaCry Ransomware: This attack affected 200,000 computers. Critical services were disrupted globally.
Black hat hacking causes severe damage. Ethical hacking protects against such threats. Understanding both helps in appreciating the need for ethical practices.
Future Trends
The world of hacking is always changing. New trends are emerging in both ethical and black hat hacking. This section explores these future trends. We will look at evolving ethical practices and emerging black hat tactics.
Evolving Ethical Practices
Ethical hackers are always improving their skills. They must stay ahead of cybercriminals. Here are some key trends:
- Artificial Intelligence (AI): AI helps ethical hackers find threats faster. It can automate complex tasks.
- Machine Learning (ML): ML improves systems over time. Ethical hackers use it to predict new threats.
- Blockchain Technology: Blockchain offers secure and transparent data. Ethical hackers use it to protect information.
- IoT Security: More devices connect to the internet. Ethical hackers work to secure these devices.
Emerging Black Hat Tactics
Black hat hackers are always finding new ways to attack. Here are some of the latest tactics:
- Advanced Ransomware: Ransomware is getting more sophisticated. Hackers demand higher ransoms.
- Phishing 2.0: Phishing attacks are becoming harder to spot. Hackers use social engineering to trick people.
- Cryptojacking: Hackers use your computer to mine cryptocurrency. This slows down your system.
- AI-Powered Attacks: Hackers use AI to find weak spots. These attacks are fast and hard to stop.
Credit: www.geeksforgeeks.org

Credit: blog.trainace.com
Frequently Asked Questions
What Is Ethical Hacking?
Ethical hacking involves authorized testing of systems to identify security vulnerabilities. It aims to improve security and protect data.
How Does Black Hat Hacking Differ?
Black hat hacking is illegal and malicious. It involves unauthorized access to systems for personal gain or to cause harm.
Why Is Ethical Hacking Important?
Ethical hacking helps organizations identify and fix security weaknesses. This prevents potential cyberattacks and data breaches.
Can Ethical Hacking Prevent Cybercrimes?
Yes, ethical hacking can prevent cybercrimes. By identifying and addressing vulnerabilities, it reduces the risk of attacks.
Conclusion
Choosing ethical hacking over black hat hacking promotes security and trust. Ethical hackers protect systems and data. Black hat hackers cause harm and legal issues. Prioritize ethical practices for a safer digital world. Always remember, the right path leads to sustainable success and a positive reputation.




Leave a Reply