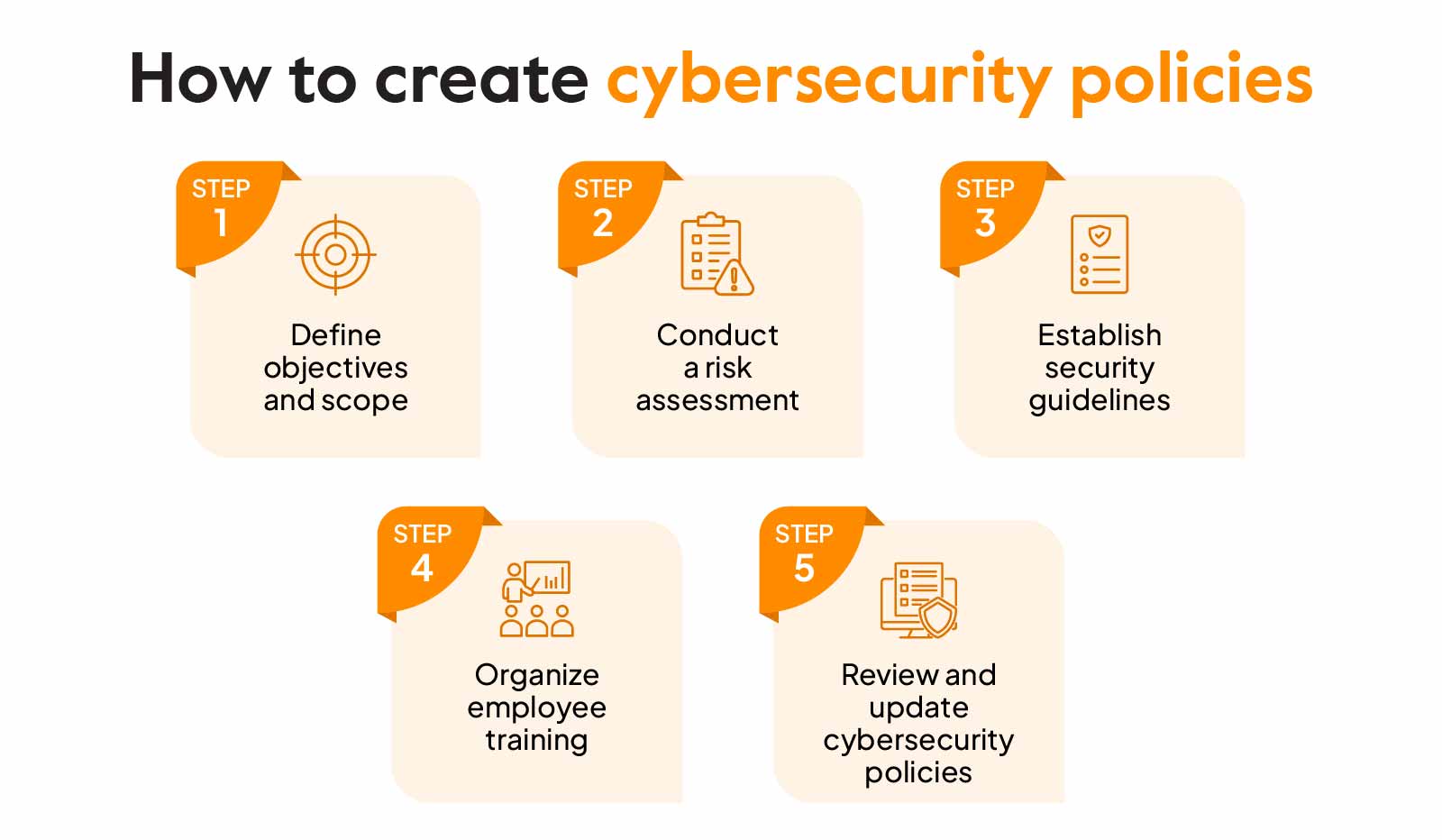
To create an effective cybersecurity policy, identify key assets and assess potential threats. Develop clear guidelines that outline acceptable use, access controls, and incident response protocols.
How to Create an Effective Cybersecurity Policy:Cybersecurity is crucial for protecting sensitive information and maintaining trust. A well-crafted policy safeguards your organization against threats and establishes a security framework. It defines responsibilities, sets expectations, and promotes a culture of security awareness among employees. Regularly updating the policy ensures it adapts to new threats and evolving technologies.
Engaging stakeholders in the development process fosters commitment and compliance. This proactive approach not only mitigates risks but also enhances overall operational resilience. By prioritizing a strong cybersecurity policy, organizations can effectively protect their digital assets and ensure long-term success.
The Importance Of Cybersecurity Policies
Cybersecurity policies are essential for any organization. They provide a framework for protecting digital assets. A strong policy helps prevent cyberattacks and reduces risks. It ensures everyone understands their roles in security.
Rising Cyber Threat Landscape
The digital world faces many dangers today. Cyber threats continue to evolve and grow. Attackers use advanced methods to breach systems.
- Ransomware attacks are on the rise.
- Phishing scams trick users into sharing data.
- Data breaches expose sensitive information.
Organizations must stay ahead of these threats. Cybersecurity policies help in identifying risks. They provide guidelines to mitigate them effectively.
Protecting Assets And Information
Every organization has valuable assets. These include data, software, and hardware. Protecting these assets is crucial for business success.
| Asset Type | Importance |
|---|---|
| Customer Data | Builds trust and loyalty. |
| Intellectual Property | Drives innovation and growth. |
| Financial Records | Ensures compliance and stability. |
A clear cybersecurity policy safeguards these assets. It outlines how to protect information. It also defines roles and responsibilities for employees.
- Train staff on security best practices.
- Establish incident response plans.
- Regularly update policies to address new threats.
Effective policies create a culture of security. Everyone becomes a part of the defense.

Credit: blog.rsisecurity.com
Initial Assessment And Risk Analysis
Creating a strong cybersecurity policy starts with an initial assessment and risk analysis. This process helps identify vulnerabilities and prioritize security measures. A thorough assessment lays the groundwork for a tailored cybersecurity policy.
Identifying Sensitive Data
Identifying sensitive data is crucial in any assessment. Sensitive data includes:
- Personal Identifiable Information (PII): Names, addresses, Social Security numbers.
- Financial Data: Credit card numbers, bank account details.
- Health Information: Medical records and health insurance details.
- Intellectual Property: Trade secrets, patents, and proprietary information.
Use a table to categorize sensitive data:
| Data Type | Examples | Impact of Breach |
|---|---|---|
| PII | Names, Social Security numbers | Identity theft, fraud |
| Financial Data | Credit card numbers | Financial loss, legal issues |
| Health Information | Medical records | Privacy violations, lawsuits |
| Intellectual Property | Trade secrets | Loss of competitive edge |
Understanding The Current Security Posture
Understanding the current security posture helps identify weaknesses. Review existing security measures and policies. Consider the following:
- Inventory of Assets: List all hardware and software.
- Security Controls: Evaluate firewalls, antivirus, and encryption.
- Incident Response Plan: Assess readiness for potential breaches.
- Employee Training: Check for cybersecurity awareness among staff.
Conduct a SWOT analysis to visualize strengths, weaknesses, opportunities, and threats:
| SWOT Analysis | Details |
|---|---|
| Strengths | Strong IT team, existing security software |
| Weaknesses | Outdated systems, lack of employee training |
| Opportunities | Invest in new technologies, training programs |
| Threats | Increased cyberattacks, regulatory changes |
Document findings for reference. This information guides the development of a robust cybersecurity policy.
Defining The Scope Of The Policy
Defining the scope of a cybersecurity policy is vital. It outlines what the policy covers. This includes who is involved and what systems are protected. A well-defined scope helps everyone understand their role in cybersecurity.
Inclusive Of All Stakeholders
Involve all stakeholders in the policy creation process. This includes:
- IT staff
- Management
- Employees
- Third-party vendors
Each group has unique insights. Their input helps create a more effective policy.
Consider using a table to identify roles:
| Stakeholder | Role |
|---|---|
| IT Staff | Implement technical controls |
| Management | Set policy direction |
| Employees | Follow daily procedures |
| Vendors | Maintain security standards |
Consistency With Business Objectives
Your cybersecurity policy must align with business goals. This ensures resources are used wisely. Consider these steps:
- Identify key business objectives.
- Assess current security measures.
- Adjust the policy to fill gaps.
Aligning the policy with business objectives helps protect assets. It also enhances overall effectiveness.
Regular reviews keep the policy relevant. Changes in business strategy or technology need updates.

Credit: www.cm-alliance.com
Key Elements Of A Strong Cybersecurity Policy
A robust cybersecurity policy protects your organization from threats. It outlines procedures and guidelines. Key elements ensure every employee understands their role in security.
Access Control Measures
Access control measures limit who can view or use information. These controls are crucial for data protection. Key aspects include:
- User Authentication: Verify users before granting access.
- Role-Based Access: Assign access based on job roles.
- Multi-Factor Authentication: Use more than one method for verification.
- Regular Audits: Check access rights periodically.
Implementing these measures minimizes risks. They help prevent unauthorized access to sensitive data.
Incident Response Planning
Incident response planning prepares your team for security breaches. This plan outlines steps to take during an incident. Key components include:
- Identify: Detect and recognize security incidents quickly.
- Contain: Limit the impact of the incident.
- Eradicate: Remove the cause of the incident.
- Recover: Restore systems to normal operations.
- Review: Analyze the incident and improve the policy.
Effective planning reduces damage and speeds recovery. Regular training ensures everyone knows their role.
Involvement Of Leadership And Employees
Creating an effective cybersecurity policy requires the active participation of both leadership and employees. Their involvement ensures that policies are realistic and practical. Engaging everyone fosters a sense of responsibility for cybersecurity. When all levels of the organization work together, they create a stronger defense against cyber threats.
Top-down Approach In Cybersecurity
A top-down approach is crucial for effective cybersecurity. Leaders must set the tone for security practices. This leadership commitment shows that cybersecurity is a priority.
- Establish clear goals for cybersecurity.
- Allocate resources to implement security measures.
- Communicate policies clearly across the organization.
- Lead by example by following security protocols.
Leadership should also regularly assess security policies. This helps identify weaknesses and adapt to new threats.
Creating A Culture Of Security Awareness
Building a culture of security awareness is essential. Employees need to understand their role in protecting the organization. Regular training sessions can enhance their skills.
| Training Topic | Frequency | Target Audience |
|---|---|---|
| Phishing Awareness | Quarterly | All Employees |
| Password Security | Bi-Annually | All Employees |
| Incident Response | Annually | IT Team |
Encourage open discussions about security. Employees should feel comfortable reporting suspicious activities. Reward those who actively participate in security initiatives.
A strong culture of security makes everyone vigilant. It ensures that cybersecurity remains a shared responsibility.
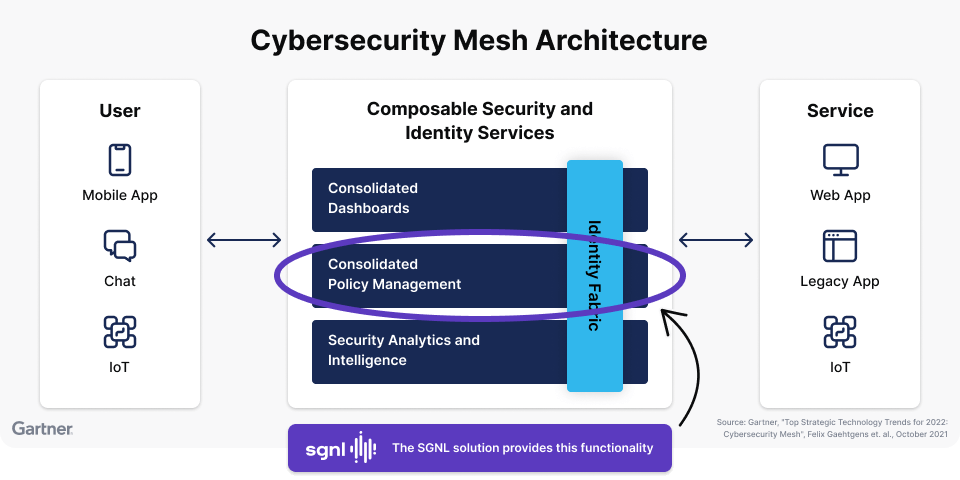
Credit: sgnl.ai
Regular Training And Awareness Programs
Regular training and awareness programs are vital for a strong cybersecurity policy. These programs empower employees to recognize threats. They also promote a culture of security within the organization. Knowledgeable employees act as the first line of defense.
Empowering Employees With Knowledge
Knowledge is power in cybersecurity. Employees must understand common threats. Here are key components for effective training:
- Identify phishing scams.
- Recognize social engineering tactics.
- Practice safe browsing habits.
- Secure personal devices.
Use engaging methods to deliver training:
- Interactive workshops
- Online courses
- Regular newsletters
Regular updates keep employees informed about new threats. Encourage questions and discussions to foster a learning environment.
Simulating Cyber Attack Scenarios
Simulations prepare employees for real-world attacks. Create realistic scenarios to test responses. This practice builds confidence and skills.
| Scenario | Objective | Frequency |
|---|---|---|
| Phishing Attack | Identify suspicious emails | Quarterly |
| Data Breach | Respond to unauthorized access | Bi-annual |
| Ransomware Attack | Implement recovery plans | Annual |
After each simulation, review responses. Discuss what went well and what needs improvement. This feedback loop enhances preparedness.
Continuous Monitoring And Review
Continuous monitoring and review are vital for an effective cybersecurity policy. They help identify risks and ensure policies remain relevant. Regular assessments can spot vulnerabilities early. This proactive approach strengthens your organization’s defenses.
Implementing Security Audits
Security audits are essential for evaluating your cybersecurity measures. These audits provide insights into current practices and highlight areas for improvement. Follow these steps to implement effective security audits:
- Schedule Regular Audits: Conduct audits at least once a year.
- Involve Experts: Use internal or external security experts.
- Document Findings: Keep detailed records of audit results.
- Address Issues: Create a plan to fix identified vulnerabilities.
- Review Audit Processes: Update procedures based on findings.
Updating The Policy To Reflect New Threats
Cyber threats evolve quickly. Your cybersecurity policy must adapt accordingly. Regular updates keep your organization protected. Consider these points when updating your policy:
- Stay Informed: Follow industry news and trends.
- Conduct Threat Assessments: Identify new and emerging threats.
- Engage Staff: Train employees about new threats and practices.
- Review Policies Regularly: Set a schedule for policy reviews.
Consider creating a table to track updates:
| Date | Update Description | Responsible Person |
|---|---|---|
| MM/DD/YYYY | Updated policy to include phishing threats. | John Doe |
| MM/DD/YYYY | Added remote work guidelines. | Jane Smith |
Regular updates ensure your cybersecurity policy remains effective. Staying vigilant helps protect sensitive information and maintain trust.
Legal Compliance And Data Protection Laws
Creating a strong cybersecurity policy involves understanding legal compliance and data protection laws. Organizations must follow these laws to protect sensitive data. Non-compliance can lead to severe penalties and loss of trust. Every business must know the rules that apply to them.
Adhering To Industry Regulations
Different industries have specific regulations. These regulations help protect data and privacy. Here are some key regulations:
- HIPAA: Applies to healthcare providers and protects patient information.
- PCI DSS: Ensures payment card data is secure.
- GDPR: Regulates data protection for individuals in the EU.
Organizations should regularly review these regulations. Regular audits help ensure compliance. Create a checklist to track adherence:
| Regulation | Compliance Status | Review Date |
|---|---|---|
| HIPAA | ✔️ Compliant | 2023-09-01 |
| PCI DSS | ❌ Non-Compliant | 2023-10-15 |
| GDPR | ✔️ Compliant | 2023-08-30 |
Global Data Privacy Requirements
Data protection laws vary across the globe. Organizations must understand these laws. Here are some global requirements:
- CCPA: Protects the privacy of California residents.
- LGPD: Regulates personal data in Brazil.
- PIPEDA: Governs data collection in Canada.
Understanding these laws is crucial. Each country has unique requirements. Ensure your policy includes:
- Data collection practices.
- Data storage and processing methods.
- Data sharing protocols.
Regular training for employees on these laws is essential. Awareness helps maintain compliance and protects your organization.
Frequently Asked Questions
What Is A Cybersecurity Policy?
A cybersecurity policy is a formal document that outlines the guidelines and protocols for protecting an organization’s digital assets. It includes rules for data protection, incident response, and user behavior. A well-crafted policy helps minimize risks and ensures compliance with legal and regulatory standards.
Why Is A Cybersecurity Policy Important?
A cybersecurity policy is crucial for safeguarding sensitive information from cyber threats. It establishes a framework for managing risks and responding to incidents. Additionally, it promotes a culture of security awareness among employees, reducing the likelihood of human error that can lead to data breaches.
How Often Should You Update Your Cybersecurity Policy?
You should update your cybersecurity policy at least annually or whenever significant changes occur. This includes updates to technology, regulations, or organizational structure. Regular reviews ensure that the policy remains relevant and effective in addressing new threats and vulnerabilities.
Who Should Be Involved In Creating The Policy?
Creating a cybersecurity policy should involve stakeholders from various departments, including IT, HR, and legal. Engaging diverse perspectives ensures that the policy addresses all potential risks. Additionally, involving upper management reinforces the importance of cybersecurity across the organization.
Conclusion
Creating an effective cybersecurity policy is essential for protecting your organization. By following clear guidelines, you empower employees to recognize and mitigate risks. Regular updates and training keep your policy relevant and effective. Invest in your cybersecurity strategy today to safeguard your data and ensure a secure future for your business.



Leave a Reply