To perform penetration testing on cloud infrastructure, start by defining the scope and identifying assets. Use automated tools and manual techniques to assess vulnerabilities and risks.
How to Perform Penetration Testing on Cloud Infrastructure:Penetration testing is essential for securing cloud environments. As businesses increasingly rely on cloud services, identifying weaknesses becomes critical. This proactive approach helps organizations safeguard sensitive data and maintain compliance. Effective penetration testing involves simulating attacks to evaluate security measures.
A thorough process includes reconnaissance, scanning, gaining access, and reporting findings. Teams should follow best practices and adhere to legal requirements. Engaging skilled professionals ensures a comprehensive assessment. By understanding vulnerabilities, organizations can fortify their cloud infrastructure and mitigate potential threats. Regular testing is vital for maintaining a robust security posture in an ever-evolving digital landscape.
Introduction To Penetration Testing In Cloud Environments
Penetration testing is vital for securing cloud infrastructure. This process identifies vulnerabilities before attackers exploit them. Organizations must ensure their cloud systems are safe. Understanding how to perform penetration testing in cloud environments is crucial.
The Critical Need For Security
Cloud services are popular among businesses. They offer flexibility and scalability. However, they also present unique security challenges.
- Data breaches can lead to significant financial loss.
- Compliance regulations require strict security measures.
- Cloud misconfigurations often expose sensitive information.
Regular penetration testing helps organizations:
- Identify security weaknesses.
- Assess the effectiveness of security controls.
- Enhance incident response strategies.
Cloud-specific Vulnerabilities
Cloud environments have unique vulnerabilities. These differ from traditional IT systems. Common cloud-specific vulnerabilities include:
| Vulnerability | Description |
|---|---|
| Insecure APIs | APIs may lack proper authentication or encryption. |
| Data Loss | Improper data handling can lead to loss or exposure. |
| Account Hijacking | Weak passwords can allow unauthorized access. |
| Misconfigured Cloud Settings | Incorrect settings can expose data to public access. |
Organizations must address these vulnerabilities. Regular testing ensures a robust security posture.
Preparation For Cloud Penetration Testing
Preparing for cloud penetration testing is crucial. It sets the stage for effective security assessments. Proper preparation helps identify vulnerabilities in cloud infrastructure. Follow these steps to ensure a successful penetration test.
Understanding Cloud Service Models
Cloud services come in three main models:
| Model | Description |
|---|---|
| IaaS | Infrastructure as a Service. Provides virtualized computing resources over the Internet. |
| PaaS | Platform as a Service. Offers hardware and software tools over the Internet. |
| SaaS | Software as a Service. Delivers software applications over the Internet. |
Each model has different security responsibilities. Understand these differences to tailor your testing approach.
Setting The Scope And Objectives
Clearly define the scope of your penetration test. This helps focus your efforts on critical areas. Consider these key points:
- Identify Assets: List all cloud resources and data.
- Determine Boundaries: Specify what is included in the test.
- Define Objectives: Establish what you want to achieve.
Common objectives include:
- Finding vulnerabilities in applications.
- Testing network security.
- Verifying data protection measures.
Engage stakeholders early. Their input can refine your scope and objectives. Ensure everyone understands the testing process and its importance.
Legal And Ethical Considerations
Penetration testing in cloud environments involves serious legal and ethical issues. Understanding these aspects is crucial. Failing to comply can lead to legal consequences. Always prioritize ethical standards during testing.
Compliance With Laws And Regulations
Each region has its own laws regarding cyber security. Familiarize yourself with these laws before testing. Here are key laws to consider:
| Law | Region | Focus |
|---|---|---|
| GDPR | European Union | Data protection and privacy |
| CCPA | California, USA | Consumer privacy rights |
| PIPEDA | Canada | Data protection and privacy |
| HIPAA | USA | Healthcare data protection |
Ensure compliance with these laws to avoid penalties. Ignoring regulations can lead to lawsuits. Consult legal experts for guidance.
Obtaining Necessary Permissions
Always seek permission before conducting penetration tests. Unauthorized testing is illegal. Follow these steps to obtain permission:
- Identify stakeholders in the cloud infrastructure.
- Draft a clear scope of work.
- Get written approval from authorized personnel.
- Document agreements and permissions.
Clear communication is vital. Discuss testing methods and timelines with stakeholders. This transparency builds trust. It also ensures everyone understands the process.
Always keep ethical standards in mind. Respect data and privacy during testing. This approach protects your organization and clients.
Selecting The Right Tools And Techniques
Choosing the right tools and techniques is vital for successful penetration testing on cloud infrastructure. The right tools improve efficiency and accuracy. Many options exist, each with unique features. Understanding these differences is essential.
Open Source Vs. Commercial Tools
Deciding between open source and commercial tools affects your testing process. Both types have strengths and weaknesses. Here’s a quick comparison:
| Feature | Open Source Tools | Commercial Tools |
|---|---|---|
| Cost | Free or low cost | Higher cost |
| Support | Community support | Dedicated support teams |
| Flexibility | Highly customizable | Limited customization |
| Updates | Frequent updates | Regular updates |
Consider your budget, expertise, and requirements. Open source tools often attract beginners. Commercial tools offer robust support and features.
Automated Vs. Manual Testing Approaches
Automated and manual testing approaches each have their place. Understanding both helps in selecting the right method.
- Automated Testing:
- Fast and efficient
- Best for repetitive tasks
- Tools can miss complex vulnerabilities
- Manual Testing:
- Thorough and detailed
- Identifies complex issues
- Time-consuming and requires skilled testers
Many experts recommend a mix of both approaches. Use automated tools for initial scans. Follow up with manual testing for deeper insights.
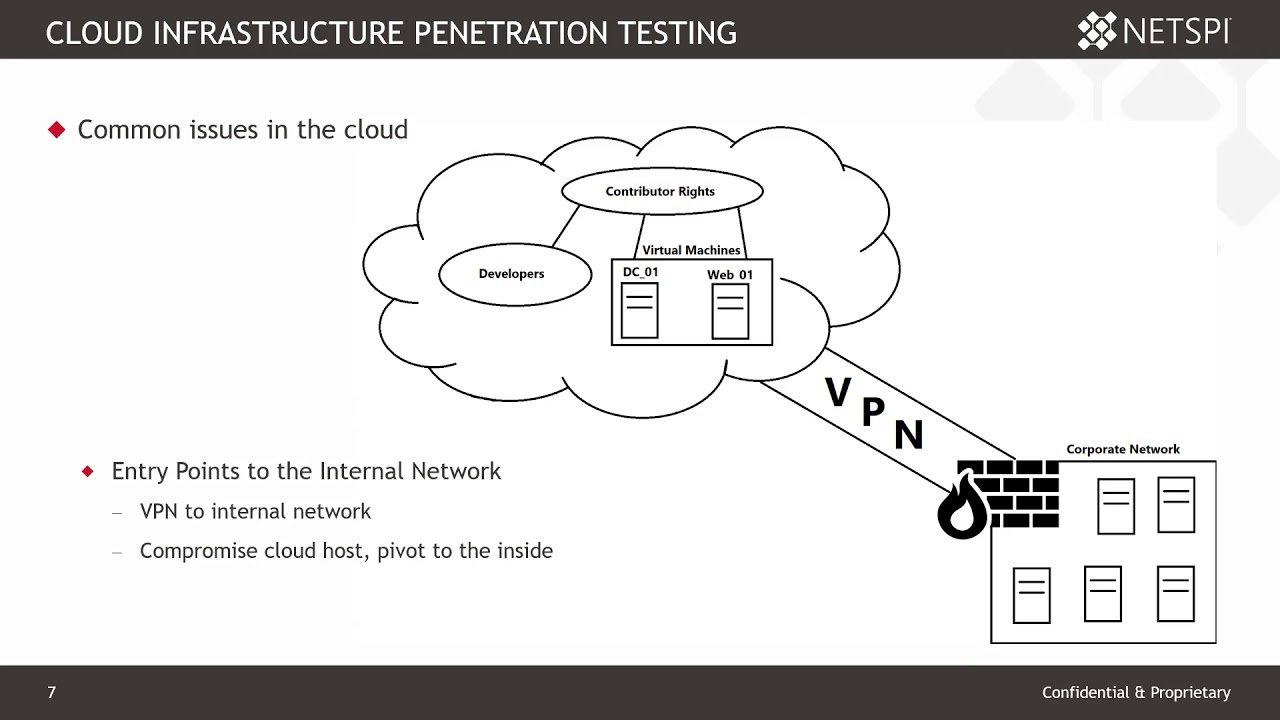
Assessment Of Cloud Infrastructure
Assessing cloud infrastructure is essential for security. Understanding its components helps identify weaknesses. Focus on two main areas: network structure and data management.
Network Structure And Access Points
The network structure defines how data flows. Identify all access points. These points can be vulnerable to attacks. Common access points include:
- Virtual Private Networks (VPNs)
- Application Programming Interfaces (APIs)
- Web applications
- Remote Desktop Protocol (RDP) connections
Map the network layout. Use tools like:
- Network diagram software
- Port scanning tools
- Traffic analysis tools
Assess firewall rules and settings. Check for:
| Firewall Configuration | Importance |
|---|---|
| Inbound rules | Control access to services |
| Outbound rules | Prevent data leakage |
Perform tests to find vulnerabilities. Use penetration testing tools like:
- Nmap
- Burp Suite
- Metasploit
Data Storage And Management
Data storage is a critical area. Assess where data is stored. Cloud providers offer various storage options:
- Block storage
- Object storage
- File storage
Review data management practices. Check for:
- Data encryption
- Access controls
- Backup procedures
Implement strong access controls. Use role-based access control (RBAC). Limit user permissions based on job roles. Maintain an audit trail for data access.
Evaluate backup strategies. Ensure backups are:
| Backup Type | Frequency |
|---|---|
| Full backup | Weekly |
| Incremental backup | Daily |
Regularly test data recovery procedures. Ensure data can be restored quickly. This minimizes downtime during incidents.
Testing And Exploiting Vulnerabilities
Testing and exploiting vulnerabilities in cloud infrastructure is essential. It helps identify security weaknesses. Finding these issues allows you to fix them before attackers do.
Simulating Attacks On Different Layers
Cloud infrastructure has multiple layers. Each layer can have its own vulnerabilities. Here are the main layers to focus on:
- Application Layer: Test web applications and APIs.
- Network Layer: Check firewalls and network configurations.
- Infrastructure Layer: Examine virtual machines and storage.
Use various tools to simulate attacks. Common tools include:
| Tool Name | Purpose |
|---|---|
| Burp Suite | Web application testing |
| Nessus | Network vulnerability scanning |
| Kali Linux | Penetration testing suite |
Run tests regularly. Ensure you cover all layers. Document findings for future reference.
Identifying Common Security Gaps
Finding common security gaps is crucial. Attackers exploit these gaps often. Some common gaps include:
- Weak Passwords: Ensure passwords are strong.
- Misconfigured Settings: Check settings for cloud services.
- Unpatched Software: Keep software up to date.
Use automated tools to identify these gaps. Manual testing also helps find hidden issues. Focus on:
- Access controls
- Data encryption
- Session management
Address these vulnerabilities quickly. Protect your cloud infrastructure from threats.
Analysis And Reporting
After conducting a penetration test on cloud infrastructure, the next step is analysis and reporting. This phase reveals vulnerabilities and suggests improvements. Proper analysis helps prioritize issues based on risk. A clear report communicates findings effectively to stakeholders.
Interpreting Penetration Test Results
Understanding penetration test results is crucial. Focus on key metrics and findings. Here are some important aspects to consider:
- Severity Levels: Classify issues as critical, high, medium, or low.
- Vulnerability Types: Identify whether issues are related to misconfigurations, weak passwords, or outdated software.
- Impact Analysis: Assess how each vulnerability affects the system.
Use the following table to categorize findings:
| Vulnerability | Severity | Impact |
|---|---|---|
| Weak Encryption | High | Data Breach |
| Open Ports | Medium | Unauthorized Access |
| Outdated Software | Critical | System Compromise |
Creating A Detailed Report
A detailed report is essential for stakeholders. It should include:
- Executive Summary: Summarize key findings and recommendations.
- Methodology: Describe the testing process and tools used.
- Findings: List all vulnerabilities with details.
- Recommendations: Offer actionable steps to mitigate risks.
- Appendices: Include supporting documents and screenshots.
Make the report visually appealing. Use charts and graphs to illustrate data. Clear formatting enhances readability and understanding. Ensure the report is accessible to non-technical stakeholders.

Credit: www.future-processing.com
Remediation And Enhancing Security Posture
Effective remediation is crucial after performing penetration testing on your cloud infrastructure. Fixing vulnerabilities strengthens security. Enhancing your security posture protects sensitive data and builds trust.
Prioritizing And Addressing Findings
After testing, assess and prioritize findings. Focus on the most critical vulnerabilities first. Use the following steps:
- Severity Assessment: Classify vulnerabilities as high, medium, or low.
- Impact Analysis: Determine potential damage from each issue.
- Resource Allocation: Assign team members to address each finding.
- Action Plans: Create clear steps for remediation.
Utilize a table to summarize findings and prioritize actions:
| Vulnerability | Severity | Action |
|---|---|---|
| SQL Injection | High | Patch code immediately |
| Weak Passwords | Medium | Implement strong password policies |
| Open Ports | Low | Close unnecessary ports |
Continuous Monitoring And Improvement
Security is an ongoing process. Continuous monitoring helps identify new threats. Implement these practices:
- Regular Audits: Conduct audits frequently to find new vulnerabilities.
- Automated Tools: Use tools for real-time monitoring.
- Employee Training: Educate staff about security best practices.
- Incident Response Plan: Develop a clear plan for responding to breaches.
Evaluate and improve security measures regularly. Stay updated on the latest threats. This proactive approach helps maintain a robust security posture.
Case Studies And Real-world Scenarios
Understanding real-world scenarios helps improve your cloud security. Case studies provide insights into successful penetration tests. They reveal vulnerabilities and effective fixes. Learning from these examples guides better practices.
Successful Penetration Tests
Several companies have carried out successful penetration tests on their cloud infrastructure. Here are a few examples:
| Company | Outcome | Key Vulnerabilities Found |
|---|---|---|
| TechCorp | Identified misconfigured storage buckets | Unrestricted access to sensitive data |
| FinServ | Discovered weak IAM policies | Overly permissive user roles |
| HealthTech | Uncovered insecure APIs | Data leakage through API endpoints |
These tests helped companies secure their cloud environments. They fixed vulnerabilities and improved their security posture.
Lessons Learned And Best Practices
Each penetration test offers valuable lessons. Here are key takeaways:
- Regular Testing: Schedule tests frequently to find new vulnerabilities.
- Automate Security: Use tools to automate checks and updates.
- Involve Teams: Ensure developers understand security practices.
- Document Findings: Keep records of all vulnerabilities and fixes.
- Stay Updated: Follow the latest cloud security trends and threats.
Implementing these best practices enhances cloud security. It creates a proactive approach to protecting sensitive data.
Credit: blog.securelayer7.net
Future Of Cloud Penetration Testing
The future of cloud penetration testing is evolving quickly. As technology advances, so do the threats. Organizations must adapt their strategies to protect sensitive data. Embracing new tools and methods is crucial for maintaining security.
Emerging Threats And Technologies
New threats are always on the horizon. Cloud environments are attractive targets for hackers. Here are some notable trends:
- Ransomware Attacks: Cybercriminals hold data hostage for money.
- Supply Chain Attacks: Targeting third-party vendors to access main systems.
- Misconfigured Cloud Settings: These can expose sensitive information.
Technologies help combat these threats. Some key technologies include:
| Technology | Purpose |
|---|---|
| Cloud Security Posture Management (CSPM) | Identifies misconfigurations in cloud setups. |
| Web Application Firewalls (WAF) | Filters and monitors HTTP traffic to protect apps. |
| Security Information and Event Management (SIEM) | Analyzes security alerts in real time. |
The Role Of Ai And Machine Learning
AI and machine learning are game-changers in cybersecurity. They help identify and respond to threats faster. Here’s how they contribute:
- Threat Detection: AI can analyze large data sets quickly.
- Anomaly Detection: Machine learning spots unusual patterns in cloud behavior.
- Automated Responses: AI can initiate responses to threats instantly.
Organizations must leverage these technologies. They enhance penetration testing efforts significantly. Investing in AI tools is a smart move for future security.
Credit: www.ssl2buy.com
Frequently Asked Questions
What Is Penetration Testing In Cloud Environments?
Penetration testing in cloud environments involves simulating cyberattacks to identify vulnerabilities. This process helps organizations understand their security posture. By uncovering weaknesses, businesses can strengthen their defenses against potential threats. Regular testing is vital for maintaining compliance and ensuring data protection.
Why Is Cloud Penetration Testing Important?
Cloud penetration testing is crucial for identifying security gaps. With increasing cloud adoption, organizations face new vulnerabilities. Regular testing helps in compliance with regulations and industry standards. It also enhances overall security posture and builds trust with clients. Ultimately, it protects sensitive data from cyber threats.
How Often Should I Perform Cloud Penetration Tests?
Organizations should conduct cloud penetration tests at least annually. However, testing frequency may vary based on changes in infrastructure or regulations. After significant updates or deployments, it’s wise to retest. Continuous monitoring and periodic assessments help maintain a robust security posture in the cloud.
What Tools Are Used For Cloud Penetration Testing?
Various tools assist in cloud penetration testing, including Nessus and Burp Suite. These tools help identify vulnerabilities and assess security configurations. Other popular options include OWASP ZAP and Metasploit. Choosing the right tool depends on specific testing requirements and cloud service models.
Conclusion
Effective penetration testing is essential for securing cloud infrastructure. By following best practices, you can identify vulnerabilities before they become threats. Regular testing not only enhances security but also builds trust with clients. Stay proactive and ensure your cloud environment remains safe from potential attacks.
Prioritize security today for a stronger tomorrow.



Leave a Reply