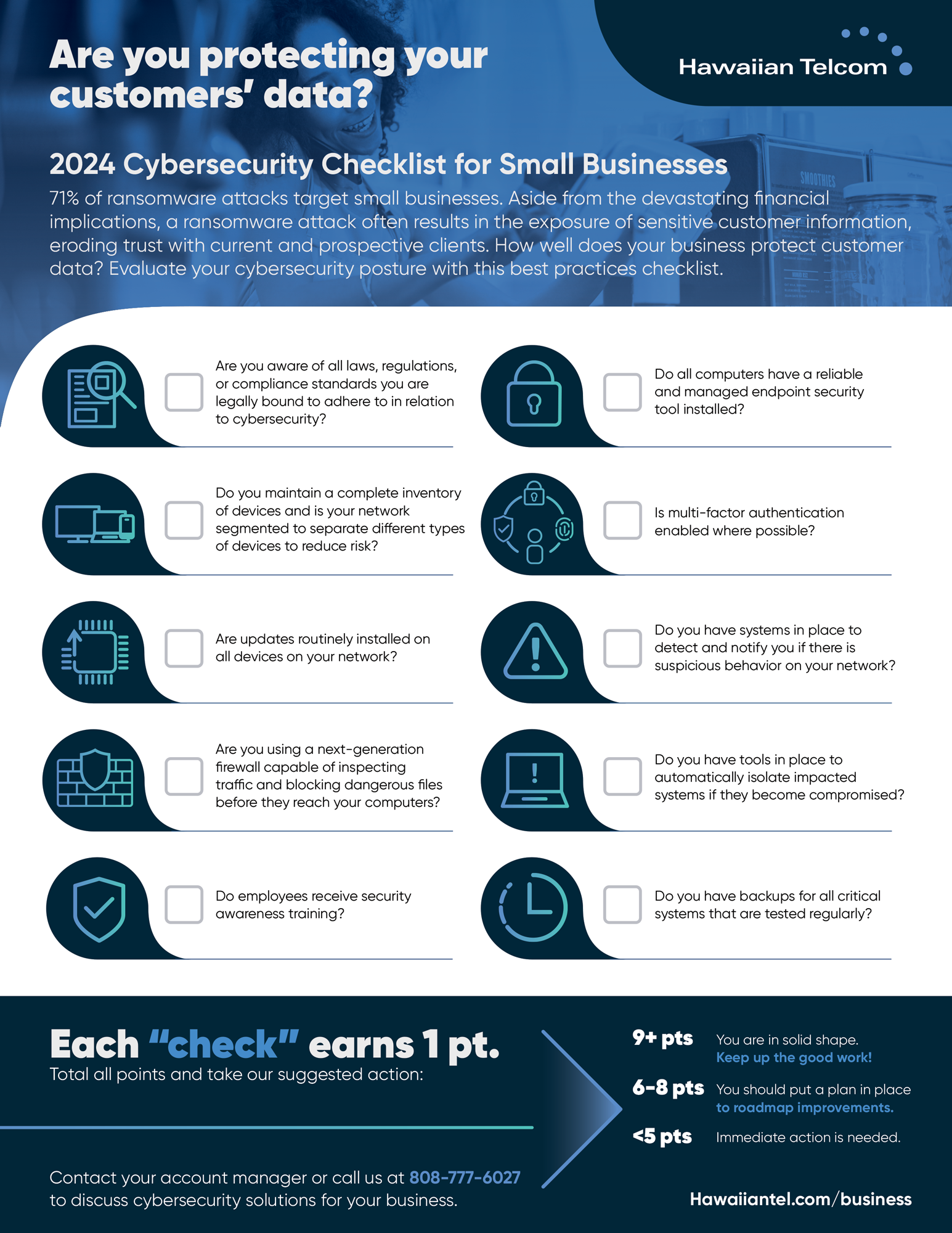
To ensure robust network security for small businesses in 2024, prioritize regular software updates and employee training. Implement strong passwords and multi-factor authentication to enhance data protection.
Best Practices for Small Business Network Security in 2024:As cyber threats continue to evolve, small businesses must adopt effective network security practices. A single breach can lead to significant financial losses and damage a company’s reputation. In 2024, safeguarding sensitive information is crucial for maintaining customer trust. Small businesses often lack the resources of larger firms, making them attractive targets for cybercriminals.
By focusing on proactive measures, such as regular updates and employee education, businesses can create a strong defense. Implementing strong passwords and multi-factor authentication adds layers of security. These practices not only protect data but also ensure compliance with regulations, ultimately fostering a safer business environment.
Credit: blog.hawaiiantel.com
The Cybersecurity Landscape In 2024
The cybersecurity landscape in 2024 is evolving rapidly. Small businesses face new challenges. Cyber threats are becoming more sophisticated. Understanding these threats is crucial for protection.
Emerging Threats To Small Businesses
Small businesses are prime targets for cybercriminals. Here are some key threats to watch:
- Ransomware Attacks: Malicious software locks data. Businesses must pay to regain access.
- Phishing Scams: Fraudulent emails trick employees. They often lead to data breaches.
- IoT Vulnerabilities: Internet-connected devices can be hacked. They may provide backdoor access to networks.
- Supply Chain Attacks: Hackers exploit weaknesses in third-party vendors. This can affect multiple businesses.
Importance Of Robust Network Security
Robust network security protects business data. It builds customer trust. Key benefits include:
- Data Protection: Safeguarding sensitive information is essential.
- Compliance: Meeting regulations avoids legal issues.
- Business Continuity: Strong security ensures operations run smoothly.
- Reputation Management: A secure network enhances business credibility.
Investing in security measures is not optional. It is a necessity for survival in 2024.
Essential Security Policies For Every Small Business
Small businesses face many security threats today. Having strong security policies is vital. These policies protect sensitive data and ensure business continuity. Implementing effective security measures is a necessity in 2024.
Employee Training And Awareness
Employees are the first line of defense against cyber threats. Regular training helps them recognize risks. Focus on these key areas:
- Phishing Awareness: Teach employees to spot phishing emails.
- Password Management: Encourage strong, unique passwords.
- Device Security: Ensure devices are secure and locked.
Conduct training sessions at least quarterly. Use real-life examples to make learning engaging. Foster a culture of security awareness within the team.
Regular Update And Patch Management
Keeping software up-to-date is critical. Updates fix vulnerabilities that hackers exploit. Follow these best practices:
- Schedule Regular Updates: Set a monthly schedule for updates.
- Automate Patching: Use tools to automate software updates.
- Monitor Software Performance: Check for issues after updates.
Neglecting updates can lead to security breaches. Create a checklist for managing software and system updates. Ensure all software is patched promptly.
Advanced Security Measures To Consider
As cyber threats evolve, small businesses must adapt their security strategies. Implementing advanced security measures is essential. These measures enhance protection against data breaches and cyber attacks.
Implementing Multi-factor Authentication
Multi-Factor Authentication (MFA) adds an extra layer of security. It requires users to verify their identity through two or more methods.
- Something you know (password)
- Something you have (smartphone or token)
- Something you are (fingerprint or facial recognition)
Using MFA significantly reduces unauthorized access. Here are some key benefits:
| Benefit | Description |
|---|---|
| Increased Security | Harder for hackers to gain access. |
| User Confidence | Employees feel safer knowing their data is protected. |
| Compliance | Helps meet regulatory requirements. |
Deploying Next-gen Firewalls
Next-Gen Firewalls offer advanced protection compared to traditional firewalls. They analyze network traffic in real-time.
- Inspect incoming and outgoing data.
- Identify and block threats.
- Prevent unauthorized access.
Consider these features for your firewall:
- Application Awareness: Understands the applications in use.
- Intrusion Prevention: Blocks potential threats automatically.
- SSL Inspection: Analyzes encrypted traffic for hidden risks.
Next-gen firewalls help maintain a secure network environment. They adapt to new threats quickly. Investing in them is a smart choice for small businesses.
Risk Assessment And Management
Small businesses face many security threats. Risk assessment helps identify these threats. Effective management minimizes their impact. This section covers best practices for assessing and managing risks.
Conducting Periodic Security Audits
Regular security audits are crucial. They help find vulnerabilities in your network. Follow these steps for effective audits:
- Identify Assets: List all hardware and software.
- Evaluate Security Controls: Check firewalls and antivirus software.
- Review Access Controls: Ensure only authorized personnel can access data.
- Analyze Logs: Monitor user activity and system changes.
- Document Findings: Keep records of vulnerabilities and fixes.
Consider using these tools for audits:
| Tool Name | Purpose |
|---|---|
| Wireshark | Network traffic analysis |
| Nessus | Vulnerability scanning |
| Metasploit | Penetration testing |
Creating A Disaster Recovery Plan
A disaster recovery plan protects your business. It ensures quick recovery from a security breach. Here are key components of a solid plan:
- Define Roles: Assign tasks to specific team members.
- Backup Data: Regularly back up important files.
- Communicate Plans: Share the plan with all employees.
- Test the Plan: Conduct drills to ensure effectiveness.
- Review and Update: Regularly revise the plan based on new threats.
Set a timeline for testing your plan:
- Monthly: Backup verification
- Quarterly: Full plan test
- Annually: Comprehensive review
Leveraging Encryption For Data Protection
Encryption is vital for protecting sensitive data. It transforms information into unreadable code. Only authorized users can access the original data. In 2024, small businesses must prioritize encryption. Cyber threats continue to rise, putting data at risk.
Encrypting Sensitive Information
Small businesses handle various types of sensitive information:
- Customer data
- Financial records
- Employee information
Encrypting this data helps safeguard it from unauthorized access. Follow these steps to encrypt sensitive information:
- Identify sensitive data types.
- Choose a strong encryption method.
- Implement encryption tools.
- Regularly update encryption protocols.
Encryption helps maintain customer trust. It also meets legal requirements for data protection.
Best Encryption Tools For Small Businesses
Choosing the right encryption tools is essential. Here are some of the best options:
| Tool Name | Type | Best For |
|---|---|---|
| VeraCrypt | Disk encryption | Full disk encryption |
| BitLocker | Drive encryption | Windows users |
| AxCrypt | File encryption | Individual files |
| OpenSSL | Data encryption | Developers |
Evaluate each tool based on business needs. Consider ease of use, cost, and support. Implementing the right tools can enhance data security significantly.

Credit: www.sikich.com
Incorporating Cloud Security Strategies
In 2024, small businesses must embrace cloud security. Cloud solutions offer flexibility and efficiency. However, these benefits come with risks. Protecting data is crucial. Implementing strong security measures ensures safety.
Choosing Secure Cloud Service Providers
Selecting a secure cloud service provider is vital. Consider these factors:
- Data Encryption: Ensure data is encrypted both in transit and at rest.
- Compliance: Check for compliance with regulations like GDPR and HIPAA.
- Reputation: Research the provider’s reputation and customer reviews.
- Security Certifications: Look for certifications such as ISO 27001 or SOC 2.
Below is a table comparing top cloud service providers:
| Provider | Data Encryption | Compliance | Certifications |
|---|---|---|---|
| Provider A | Yes | GDPR, HIPAA | ISO 27001 |
| Provider B | Yes | GDPR | SOC 2 |
| Provider C | Yes | HIPAA | ISO 27001, SOC 2 |
Cloud Access Security Broker (casb)
A Cloud Access Security Broker (CASB) enhances security. CASBs act as a gatekeeper. They provide visibility and control over cloud applications.
Key benefits of using a CASB include:
- Data Loss Prevention: Prevent unauthorized data access.
- Threat Protection: Identify and block potential threats.
- Compliance Monitoring: Ensure adherence to regulations.
- Access Control: Manage who can access what data.
Implementing a CASB can strengthen your cloud security posture. It ensures your data stays safe in the cloud.
Networking Hardware Essentials
Small businesses need strong network security. Using the right hardware is key. Here are some essential practices for 2024.
Upgrading To Advanced Routers
Outdated routers can expose your business to risks. Upgrading to advanced routers provides better security features.
- Firewall Protection: Built-in firewalls block unauthorized access.
- VPN Support: Secure remote connections for employees.
- Quality of Service (QoS): Prioritize important traffic for smooth operations.
Choose routers that support the latest Wi-Fi standards. Look for Wi-Fi 6 or higher. These offer improved speed and capacity.
Securing Wireless Access Points
Wireless access points (WAPs) can be vulnerable. Securing them is crucial for network safety.
- Change Default Passwords: Use strong, unique passwords.
- Enable WPA3 Encryption: This offers better security than older methods.
- Disable SSID Broadcasting: Hide your network from prying eyes.
Regularly update the firmware on all WAPs. Keeping software up to date fixes security flaws.
Use a table to summarize key features:
| Feature | Description |
|---|---|
| Firewall Protection | Blocks unauthorized access to your network. |
| VPN Support | Secures remote connections for employees. |
| WPA3 Encryption | Provides strong security for wireless networks. |
Implement these practices to enhance your small business network security.
Monitoring And Incident Response
Effective monitoring and swift incident response are key to small business network security in 2024. These practices help identify threats and address them quickly. Implementing robust systems protects valuable data and minimizes potential damage.
Implementing Intrusion Detection Systems
Intrusion Detection Systems (IDS) act as security guards for your network. They monitor for suspicious activity and alert you immediately. Here are some benefits of using IDS:
- Real-time monitoring: Detect threats as they happen.
- Automated alerts: Receive instant notifications about breaches.
- Data analysis: Understand patterns in attacks to improve security.
Choose between two types of IDS:
| Type of IDS | Description |
|---|---|
| Network-based IDS | Monitors network traffic for suspicious activity. |
| Host-based IDS | Monitors activities on individual devices. |
Developing A Swift Incident Response Protocol
A strong incident response protocol is essential. This plan should outline steps to take during a security breach. Ensure every employee understands their role. Here are key steps to include:
- Preparation: Train staff on security best practices.
- Identification: Quickly determine the type of breach.
- Containment: Limit the damage by isolating affected systems.
- Eradication: Remove the threat from the network.
- Recovery: Restore systems and data to normal operation.
- Lessons Learned: Analyze the incident to improve future responses.
Regularly review and update your incident response plan. This keeps it effective against new threats. Engage your team in drills to enhance readiness.
Compliance And Legal Considerations
Small businesses must prioritize compliance and legal considerations in 2024. Ensuring network security not only protects your business but also builds trust with customers. Understanding industry regulations is key to safeguarding your operations.
Understanding Industry Regulations
Different industries have unique regulations regarding data protection. Familiarize yourself with the specific laws that apply to your business. Here are some important regulations:
- GDPR – Applies to businesses handling EU customer data.
- HIPAA – Relevant for healthcare-related organizations.
- PCI DSS – Required for businesses accepting credit card payments.
Non-compliance can lead to severe penalties. Regular training for employees is essential. Create a compliance checklist to track requirements.
Protecting Customer Data And Privacy
Customer data protection is crucial for maintaining trust. Implement these best practices:
- Encrypt sensitive information to prevent unauthorized access.
- Regularly update software to fix security vulnerabilities.
- Limit data access to only those who need it.
- Conduct regular audits of your data protection measures.
Use a table to summarize key data protection strategies:
| Strategy | Benefits |
|---|---|
| Data Encryption | Protects data from breaches |
| Software Updates | Fixes security flaws |
| Access Control | Reduces data exposure risks |
| Regular Audits | Ensures compliance and security |
Implementing these strategies protects customer data and fosters loyalty. Stay informed about changes in laws that affect your business.

Credit: infoseclabs.io
Staying Informed And Proactive
Small businesses face constant threats in the digital world. Staying informed and proactive is key to network security. Awareness helps prevent attacks and data breaches. Regular updates protect your business from evolving threats.
Subscribing To Security Bulletins
Security bulletins provide essential information about threats. Here are some benefits:
- Receive alerts on new vulnerabilities.
- Get tips on security best practices.
- Stay updated on software patches.
Many reputable sources offer security bulletins:
| Source | Description |
|---|---|
| US-CERT | Alerts on cybersecurity incidents and vulnerabilities. |
| CVE | A database of known vulnerabilities. |
| Vendor Bulletins | Updates from software and hardware vendors. |
Subscribing to these bulletins helps you stay secure. It keeps your business informed about the latest threats.
Joining Small Business Cybersecurity Groups
Connecting with others improves your network security. Small business cybersecurity groups offer support and resources. Benefits include:
- Sharing best practices.
- Accessing training and resources.
- Networking with cybersecurity professionals.
Consider these types of groups:
- Local Chamber of Commerce groups.
- Online forums and discussion boards.
- Social media groups focused on cybersecurity.
These groups keep you informed and proactive. Learning from others helps you strengthen your security measures.
Frequently Asked Questions
What Are Small Business Network Security Best Practices?
Small businesses should implement strong password policies and utilize multi-factor authentication. Regularly update software and hardware to protect against vulnerabilities. Conduct employee training to recognize phishing attempts. Lastly, maintain regular backups and establish a clear incident response plan to ensure data recovery.
How Can I Secure My Small Business Network?
To secure your network, start by using a firewall and enabling encryption on all devices. Regularly monitor network traffic for unusual activity. Update all passwords frequently, and restrict access to sensitive data. Also, consider investing in a VPN for remote employees to enhance security.
Why Is Network Security Important For Small Businesses?
Network security is crucial because small businesses are prime targets for cyberattacks. A breach can lead to significant financial losses and damage to your reputation. Ensuring data protection builds customer trust and complies with regulations. Ultimately, strong security measures safeguard your assets and business continuity.
What Are Common Network Security Threats?
Common threats include phishing attacks, malware, ransomware, and unauthorized access. Insider threats and social engineering are also prevalent. Recognizing these risks is essential for developing effective security strategies. Regularly updating your security protocols can mitigate these threats and enhance your defenses.
Conclusion
Securing your small business network is crucial in 2024. Implementing strong passwords, regular updates, and employee training can significantly reduce risks. Stay informed about the latest threats and invest in reliable security tools. By prioritizing network security, you protect your business and build trust with your customers.
Make security a top priority today.




Leave a Reply