To prevent data breaches in cloud computing environments, implement strong encryption and regular security audits. User access controls and employee training are also essential.
Preventing Data Breaches in Cloud Computing Environments:Cloud computing offers significant advantages, but it also presents unique security challenges. Data breaches can lead to severe consequences, including financial loss and reputational damage. Organizations must prioritize data protection to maintain trust and compliance. Effective strategies include employing encryption technologies, conducting regular security assessments, and establishing clear access controls.
Educating employees about security best practices further enhances protection against potential threats. By proactively addressing vulnerabilities, businesses can safeguard their sensitive information and ensure a secure cloud environment. A comprehensive approach to security not only mitigates risks but also fosters a culture of accountability and vigilance within the organization.
The Rise Of Cloud Computing
The world is rapidly shifting to cloud computing. Businesses and individuals now prefer cloud services over traditional methods. This trend offers flexibility and scalability. However, it brings challenges, especially in data security. Understanding these changes is crucial for everyone.
Shift To Cloud Services
Many organizations are moving to the cloud for various reasons:
- Cost Efficiency: Reduces hardware costs.
- Accessibility: Access data from anywhere.
- Collaboration: Teams can work together in real-time.
- Scalability: Easily adjust resources as needed.
This shift is not just a trend; it’s a necessity. Companies want to stay competitive and agile. The cloud provides the tools to achieve that.
Data Security Concerns
As more data moves to the cloud, security risks increase. Key concerns include:
- Data Breaches: Unauthorized access to sensitive information.
- Loss of Control: Organizations may lose oversight of data.
- Compliance Issues: Failing to meet regulations can lead to fines.
- Insider Threats: Employees may misuse access to data.
Organizations must address these concerns. They should implement strong security measures. Here are some strategies to enhance data security:
| Strategy | Description |
|---|---|
| Encryption | Protect data by converting it into a secure format. |
| Multi-Factor Authentication | Require multiple forms of verification for access. |
| Regular Audits | Perform checks to ensure data security compliance. |
| Employee Training | Educate staff about security best practices. |
Addressing these security concerns is vital. Organizations must safeguard their data effectively.
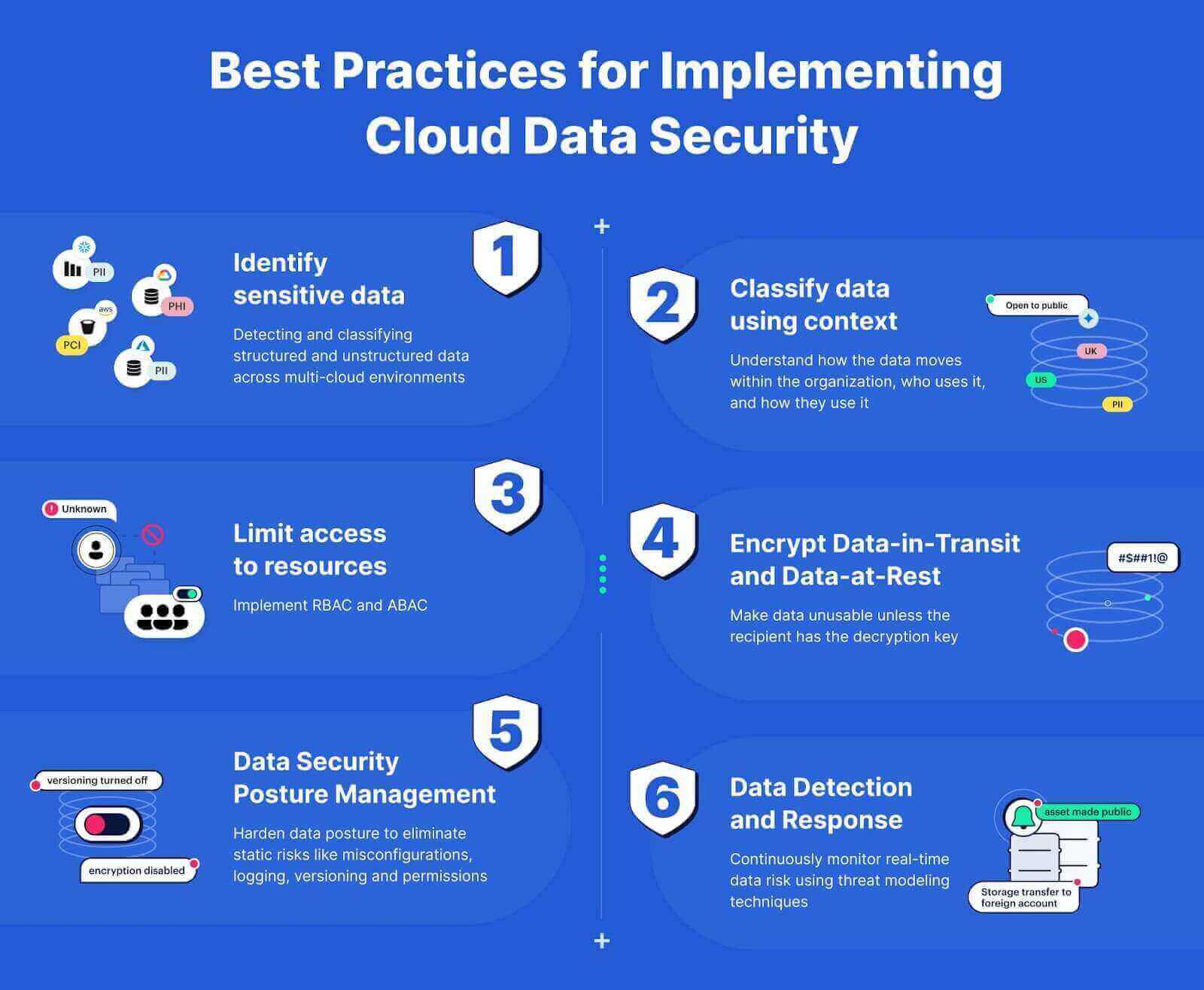
Credit: www.paloaltonetworks.com
Data Breaches: A Grim Reality
Data breaches are a serious threat in cloud computing. They can cause massive damage to businesses. Understanding the risks is crucial. Awareness can help prevent them.
Recent Breach Statistics
Data breaches are becoming more frequent. Here are some shocking statistics:
| Year | Number of Breaches | Average Cost per Breach |
|---|---|---|
| 2021 | 18 million | $4.24 million |
| 2022 | 25 million | $4.35 million |
| 2023 | 30 million | $4.45 million |
These statistics show that breaches are rising. Each year, costs increase too. Businesses must take action.
Impact On Businesses
Data breaches affect businesses in many ways:
- Financial Loss: Companies lose money due to breaches.
- Reputation Damage: Customers lose trust in affected brands.
- Legal Issues: Breaches can lead to lawsuits.
- Operational Disruption: Breaches can halt business operations.
Businesses must prioritize data security. Ignoring the risks can lead to severe consequences. Protecting data should be a top focus.
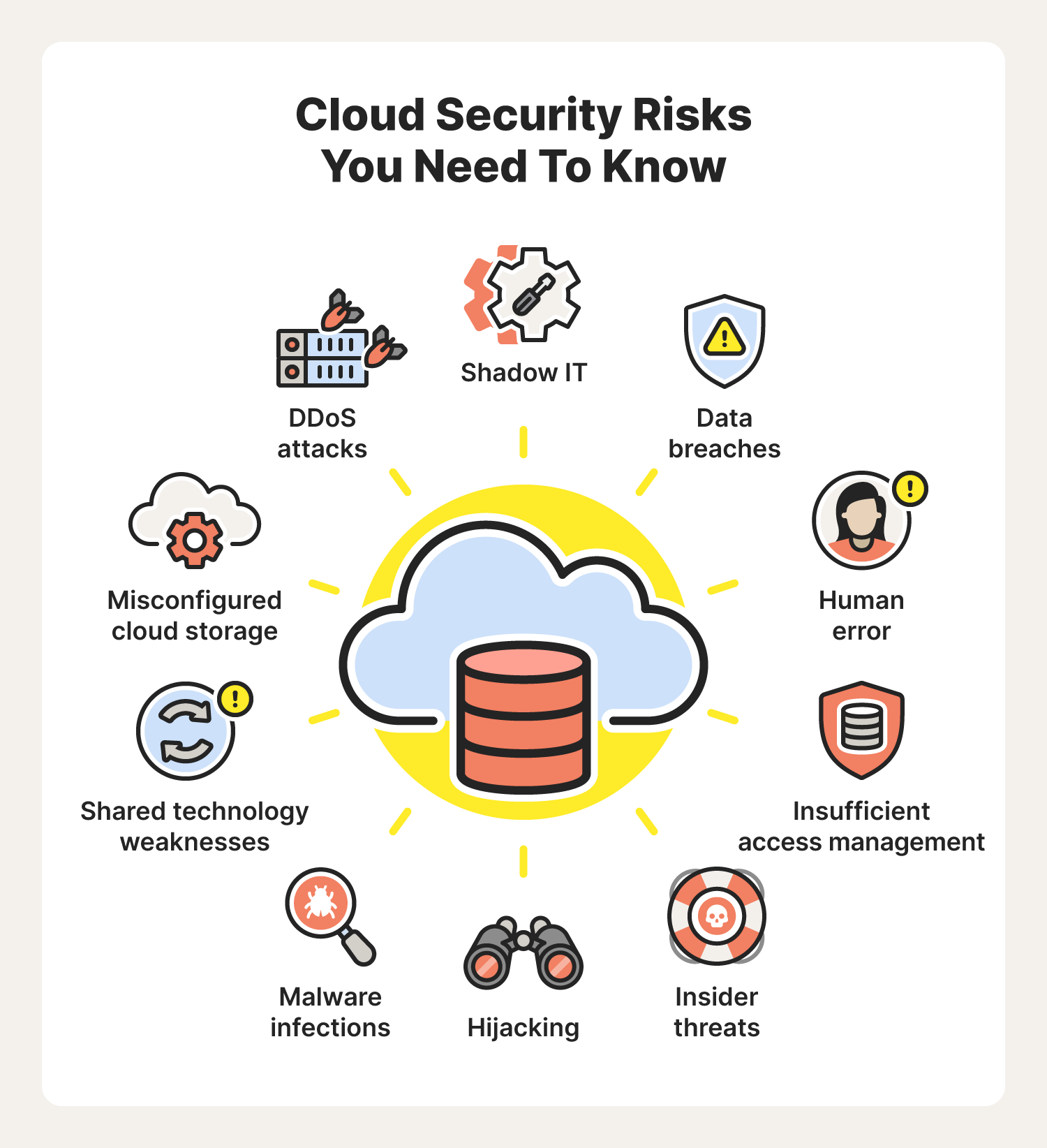
Key Vulnerabilities In Cloud Systems
Cloud computing offers many benefits. Yet, it has key vulnerabilities. Understanding these weaknesses helps prevent data breaches. Let’s explore two significant vulnerabilities: Misconfigured Cloud Storage and Inadequate Access Controls.
Misconfigured Cloud Storage
Misconfigurations are one of the top reasons for data breaches. Simple mistakes can expose sensitive data. Common misconfigurations include:
- Public access to private data
- Weak storage policies
- Unsecured APIs
These errors can lead to serious issues. Regular audits can help find and fix misconfigurations. Consider these steps:
- Review permissions frequently.
- Use automated tools for monitoring.
- Implement strict access policies.
Inadequate Access Controls
Access controls are crucial in cloud systems. Poorly managed access can lead to unauthorized data access. Key problems include:
- Weak password policies
- Lack of multi-factor authentication
- Overly broad user permissions
To strengthen access controls, take these actions:
| Action | Description |
|---|---|
| Set strong passwords | Use at least 12 characters with symbols. |
| Enable multi-factor authentication | Require a second form of identity verification. |
| Limit user permissions | Grant access only to necessary users. |
Implementing these measures can help keep data safe. Stay vigilant about access controls and configurations.
Essential Security Practices
Data breaches can harm businesses and individuals. Implementing essential security practices helps protect sensitive information. These practices focus on proactive measures to secure cloud computing environments.
Regular Security Audits
Regular security audits are critical for identifying vulnerabilities. Audits help ensure compliance with security standards.
- Schedule audits quarterly or bi-annually.
- Involve third-party security experts.
- Review access controls and permissions.
- Test for potential weaknesses in the system.
Use the following table to track your audit findings:
| Audit Date | Findings | Actions Taken |
|---|---|---|
| 01/01/2023 | Weak passwords identified | Implemented stronger password policies |
| 07/01/2023 | Unpatched software | Updated all software components |
Encryption Strategies
Encryption protects data during storage and transmission. It ensures that only authorized users can access sensitive information.
- Use AES (Advanced Encryption Standard) for data at rest.
- Implement TLS (Transport Layer Security) for data in transit.
Consider these steps to enhance encryption:
- Regularly update encryption keys.
- Use different keys for different data types.
- Monitor access to encryption keys.
Encrypting data significantly reduces the risk of exposure. It adds an essential layer of security to your cloud environment.
Advanced Threat Detection Techniques
Advanced threat detection techniques help protect cloud environments. They identify potential risks quickly. This keeps data safe from breaches. Two key methods are AI and machine learning, along with behavioral analytics.
Ai And Machine Learning
Artificial Intelligence (AI) and machine learning play vital roles in threat detection. They analyze vast amounts of data. This helps find unusual patterns and behaviors. Here are key benefits:
- Fast Detection: AI systems can spot threats in real-time.
- Predictive Analysis: They predict future attacks based on past data.
- Continuous Learning: Machine learning improves detection over time.
These systems reduce false positives. They focus on genuine threats. AI and machine learning adapt to new attack methods.
Behavioral Analytics
Behavioral analytics examines user activities. It creates a profile of normal behavior. This helps detect anomalies. Key points include:
| Feature | Description |
|---|---|
| Activity Monitoring | Tracks user actions in real-time. |
| Anomaly Detection | Identifies unusual patterns that could indicate threats. |
| Risk Scoring | Assigns scores to activities based on risk levels. |
Behavioral analytics helps organizations respond quickly. It reveals insider threats and compromised accounts. This method strengthens cloud security.
Incident Response Planning
Incident response planning is crucial for cloud security. A solid plan helps organizations react swiftly to data breaches. This reduces damage and recovery time. Proper planning ensures teams know their roles during an incident.
Developing A Response Strategy
Creating a strong response strategy involves several key steps:
- Identify Critical Assets: List all vital data and applications.
- Define Roles: Assign clear roles to team members.
- Establish Communication Plans: Ensure everyone knows how to communicate.
- Set Recovery Objectives: Define recovery time and data loss limits.
A well-defined strategy helps teams act quickly. This minimizes confusion during an incident. Regular updates keep the strategy relevant.
Simulation Exercises
Regular simulation exercises enhance readiness. These exercises test the response strategy in real-life scenarios.
Benefits of simulation exercises include:
- Identifying gaps in the response plan
- Improving team collaboration
- Boosting confidence in handling incidents
Schedule these exercises at least twice a year. Include all stakeholders in the process. Track performance and make improvements.
| Exercise Type | Frequency | Purpose |
|---|---|---|
| Tabletop Exercises | Quarterly | Discuss scenarios and decision-making |
| Full-Scale Drills | Biannually | Test the entire incident response |
Simulation exercises prepare teams for actual incidents. They ensure everyone knows their roles and responsibilities.
Fostering A Culture Of Security
Creating a culture of security is essential in cloud computing. It involves everyone in the organization. Employees must understand their role in protecting data. This culture helps prevent data breaches and builds trust.
Training And Awareness Programs
Regular training keeps employees informed about security risks. Awareness programs help staff recognize threats. Here are key elements:
- Regular Workshops: Offer workshops on cloud security.
- Interactive Sessions: Use real-life scenarios for better understanding.
- Quizzes: Test knowledge to reinforce learning.
Consider a training schedule:
| Month | Training Topic | Duration |
|---|---|---|
| January | Introduction to Cloud Security | 2 hours |
| April | Phishing Awareness | 1 hour |
| July | Data Encryption Techniques | 3 hours |
| October | Incident Response | 2 hours |
Continuous Improvement Mindset
Security is not a one-time effort. Organizations need a continuous improvement mindset. Regular assessments help identify weaknesses. Implement changes based on findings.
Steps to foster this mindset:
- Conduct Regular Audits: Review security measures often.
- Gather Feedback: Encourage employees to share security concerns.
- Update Policies: Revise security policies as needed.
This approach keeps the organization vigilant. It strengthens the overall security posture.
Credit: us.norton.com
Regulatory Compliance And Standards
Regulatory compliance ensures that companies protect data effectively. Standards help maintain security in cloud computing environments. Understanding these regulations is crucial for preventing data breaches.
Understanding Gdpr And Ccpa
GDPR stands for General Data Protection Regulation. It applies to companies handling data of EU citizens. Key principles include:
- Data minimization: Collect only necessary data.
- Transparency: Inform users about data collection.
- User consent: Obtain clear permission from users.
CCPA is the California Consumer Privacy Act. It focuses on protecting the privacy of California residents. Important aspects include:
- Right to know: Users can request information about their data.
- Right to delete: Users can ask for their data to be removed.
- Opt-out: Users can refuse data sale to third parties.
| Regulation | Region | Key Focus |
|---|---|---|
| GDPR | EU | Data protection and privacy |
| CCPA | California | Consumer privacy rights |
Iso/iec 27001 Certification
ISO/IEC 27001 is an international standard for information security management. This certification helps organizations manage sensitive data securely. Benefits include:
- Improved risk management.
- Increased customer trust.
- Compliance with legal requirements.
To achieve this certification, organizations must:
- Assess current security measures.
- Identify gaps and risks.
- Implement necessary controls.
- Regularly review and improve security.
ISO/IEC 27001 certification enhances an organization’s reputation. It shows commitment to data security and compliance.
Leveraging Cloud Service Providers
Cloud service providers (CSPs) offer powerful tools for businesses. They help secure data in cloud environments. Choosing the right provider is essential. This decision affects your data security directly.
Choosing The Right Partner
Selecting a cloud service provider requires careful thought. Look for these key features:
- Security Certifications: Check for ISO 27001 or SOC 2 certifications.
- Data Encryption: Ensure data is encrypted in transit and at rest.
- Access Controls: Look for role-based access management.
- Compliance: Verify compliance with regulations like GDPR or HIPAA.
Research potential CSPs thoroughly. Review their security protocols and incident response plans. Ask about their track record with data breaches. Always prioritize security over pricing.
Collaboration For Security
Work closely with your cloud service provider. This partnership enhances security measures. Here are effective strategies:
- Regular Security Audits: Conduct audits to identify vulnerabilities.
- Shared Responsibility Model: Understand who is responsible for what.
- Incident Response Plans: Develop a joint response plan for breaches.
Establish open communication with your CSP. Share your security needs and concerns. This collaboration builds trust and strengthens defenses.
| Security Feature | Description |
|---|---|
| Data Encryption | Protects data from unauthorized access. |
| Access Controls | Limits who can see or use data. |
| Regular Updates | Keeps software secure against new threats. |
Invest time in building a strong partnership. This proactive approach reduces risks of data breaches. Your data’s safety depends on effective collaboration.
Future Of Cloud Security
The future of cloud security is evolving rapidly. Organizations face new threats daily. Emerging technologies play a key role in this transformation.
Emerging Technologies
Several technologies are reshaping cloud security. Here are the most notable:
- Artificial Intelligence (AI) – AI helps detect threats in real-time.
- Machine Learning (ML) – ML analyzes patterns to predict breaches.
- Blockchain – Blockchain enhances data integrity and security.
- Zero Trust Architecture – This model verifies every user and device.
These technologies improve security by:
- Automating threat detection.
- Reducing human error.
- Enhancing data encryption.
Predictions And Trends
Experts predict several trends for cloud security:
| Trend | Description |
|---|---|
| Increased Regulation | More laws will govern data protection. |
| Focus on Privacy | Organizations will prioritize user data privacy. |
| Rise of Multi-Cloud Strategies | Companies will use multiple cloud providers for better security. |
| Enhanced Security Training | Employees will receive more training on security best practices. |
These trends highlight the importance of proactive measures. Businesses must adapt to stay secure in the cloud.

Credit: www.aquasec.com
Frequently Asked Questions
How Can I Secure My Cloud Data?
To secure your cloud data, implement strong encryption methods. Regularly update access controls and use multi-factor authentication. Monitor user activity and conduct regular security audits. Educate your team on best practices to prevent human errors. These steps will significantly reduce the risk of data breaches.
What Are The Common Causes Of Data Breaches?
Common causes of data breaches include weak passwords, phishing attacks, and unpatched software vulnerabilities. Insider threats and misconfigured cloud settings also pose significant risks. Educating employees and using robust security protocols can mitigate these issues. Regularly review and update your security measures to stay ahead of threats.
How Does Encryption Help In Cloud Security?
Encryption protects data by converting it into an unreadable format. Only authorized users with the correct decryption keys can access the information. This adds an extra layer of security, making it difficult for unauthorized users to exploit sensitive data. Implementing encryption is essential for safeguarding your cloud environment.
What Role Do Access Controls Play In Cloud Security?
Access controls restrict who can view or modify cloud data. By implementing role-based access control, you limit access to sensitive information. This minimizes the chances of unauthorized access and potential breaches. Regularly review and adjust permissions to ensure only necessary personnel have access.
Conclusion
Data breaches in cloud computing can lead to severe consequences. Implementing robust security measures is essential for protecting sensitive information. Regular audits, employee training, and strong access controls are crucial steps. By prioritizing these strategies, businesses can significantly reduce the risk of data breaches and safeguard their cloud environments effectively.



Leave a Reply