Network security solutions for cloud-based environments include firewalls, encryption, and identity management systems. These measures protect data integrity and prevent unauthorized access.
Cloud computing has revolutionized how businesses operate, offering flexibility and scalability. However, this shift has brought new security challenges. Organizations must prioritize robust security solutions tailored for cloud environments. Effective network security is essential to safeguard sensitive data against threats like cyberattacks and data breaches.
Implementing strategies such as multi-factor authentication and real-time monitoring can significantly enhance security posture. Businesses should also consider encryption techniques to protect data both in transit and at rest. Developing a comprehensive cloud security strategy ensures that organizations can confidently harness the benefits of cloud technology while minimizing risks.
The Evolution Of Network Security In The Cloud Era
The shift to cloud computing has changed how we view network security. Traditional methods often focused on protecting physical servers. Now, security measures must adapt to a more complex environment. Cloud services offer flexibility but also introduce new risks. Understanding this evolution is crucial for effective security management.
From On-premises To Cloud: A Security Perspective
Shifting from on-premises to cloud environments transformed security strategies. Here are key differences:
| Aspect | On-Premises Security | Cloud Security |
|---|---|---|
| Control | Full control over hardware | Shared responsibility model |
| Compliance | Custom regulations | Provider-specific compliance standards |
| Cost | High upfront costs | Pay-as-you-go model |
Organizations now share security responsibilities with cloud providers. This requires clear communication and defined roles. Effective security must be proactive and not reactive.
Challenges Posed By Cloud Computing
Cloud computing presents unique challenges for network security. Some of these challenges include:
- Data Breaches: Sensitive information is vulnerable.
- Insider Threats: Employees can misuse access.
- Compliance Issues: Regulations vary by location.
- Misconfigured Settings: Errors can expose data.
- Vendor Lock-In: Difficulties in switching providers.
Each challenge requires specific solutions. Organizations must implement strong security measures. Regular audits and updates enhance security posture.
Identifying Key Threats To Cloud Environments
Cloud environments offer flexibility and scalability. Yet, they face serious security threats. Understanding these threats helps protect sensitive data. This section explores common vulnerabilities and rising cyber attack sophistication.
Common Vulnerabilities In Cloud Systems
Cloud systems have unique vulnerabilities. These weaknesses can lead to data breaches and service disruptions. Here are some common vulnerabilities:
- Misconfigured Cloud Settings: Incorrect settings can expose data.
- Insecure APIs: Weak APIs can be exploited by attackers.
- Insufficient Identity Management: Poor access controls increase risks.
- Data Loss: Accidental deletions or corruption can occur.
- Shared Technology Vulnerabilities: Multi-tenant environments can spread risks.
Awareness of these vulnerabilities is crucial. Organizations must assess their cloud configurations regularly. Proper security measures can mitigate these risks.
Rising Sophistication Of Cyber Attacks
Cyber attacks are becoming more complex. Attackers use advanced techniques to breach cloud systems. Key trends include:
- Phishing Attacks: Deceptive emails trick users into revealing credentials.
- Ransomware: Attackers encrypt data and demand payment.
- Distributed Denial of Service (DDoS): Overloading systems to disrupt services.
- Advanced Persistent Threats (APTs): Long-term attacks targeting specific organizations.
Organizations must stay informed about these threats. Regular training for employees is vital. Strong security protocols can help defend against these sophisticated attacks.
Core Principles Of Cloud Network Security
Understanding the core principles of cloud network security is vital. These principles ensure data protection in cloud environments. They help manage risks and secure sensitive information.
The Shared Responsibility Model
The Shared Responsibility Model defines security roles between the cloud provider and the user. It helps clarify who is responsible for what.
- Cloud Provider: Responsible for security of the cloud infrastructure.
- User: Responsible for securing their data and applications.
This model varies by service type:
| Service Type | Provider Responsibilities | User Responsibilities |
|---|---|---|
| Infrastructure as a Service (IaaS) | Physical security, network, and virtualization | Operating system, applications, and data |
| Platform as a Service (PaaS) | Physical and network security | Applications and data |
| Software as a Service (SaaS) | Application security and infrastructure | User data and access control |
Essential Security Policies For Cloud Deployment
Implementing essential security policies is crucial for cloud deployment. These policies help protect data and maintain compliance.
- Data Encryption: Protect data at rest and in transit.
- Access Control: Use role-based access for users.
- Incident Response Plan: Prepare for potential security breaches.
- Regular Audits: Conduct audits to identify vulnerabilities.
- Compliance: Follow regulations like GDPR and HIPAA.
These policies create a secure cloud environment. They help organizations trust their cloud services.
Strategic Layers Of Defense For Cloud Networks
Cloud networks require multiple layers of defense. These layers protect data and applications from various threats. A strong strategy ensures that each layer works together seamlessly.
Implementing Firewalls And Intrusion Detection Systems
Firewalls are essential for safeguarding cloud networks. They monitor incoming and outgoing traffic. This helps block unauthorized access.
- Types of Firewalls:
- Network-based Firewalls
- Application-based Firewalls
Intrusion Detection Systems (IDS) add another layer of security. They detect suspicious activity in real-time. An IDS alerts administrators about potential breaches.
Key benefits include:
- Real-time threat detection.
- Reduced response time to incidents.
- Improved overall network security.
Encryption: Protecting Data In Transit And At Rest
Encryption is vital for cloud security. It protects sensitive data both in transit and at rest. This means data is secure while being transferred and stored.
| Encryption Type | Purpose |
|---|---|
| Symmetric Encryption | Uses the same key for encryption and decryption. |
| Asymmetric Encryption | Uses a public key for encryption and a private key for decryption. |
Benefits of encryption include:
- Data confidentiality.
- Data integrity.
- Compliance with regulations.
Implementing these security measures creates a robust defense. It helps protect cloud networks from potential threats.
Advanced Network Security Technologies
Advanced network security technologies protect cloud-based environments effectively. These solutions use innovative methods. They enhance data safety and reduce risks. Key technologies include AI, machine learning, and blockchain.
Ai And Machine Learning For Threat Detection
AI and machine learning (ML) are game-changers in security. They analyze data patterns quickly. These technologies find threats faster than humans. Here are some benefits:
- Real-time analysis: Detects threats as they happen.
- Predictive capabilities: Anticipates potential attacks.
- Automated responses: Takes action without human input.
AI systems learn from past incidents. They adapt to new threats. This continuous learning helps build stronger defenses. A simple example:
| Feature | Benefit |
|---|---|
| Data Analysis | Identifies unusual behavior. |
| Incident Response | Reduces response time. |
Blockchain For Enhanced Security Measures
Blockchain technology offers unique security features. It provides a decentralized approach. This reduces single points of failure. Key benefits include:
- Data integrity: Ensures data cannot be altered.
- Transparency: Allows all users to see transactions.
- Enhanced privacy: Protects user identities effectively.
Blockchain creates secure logs. These logs are tamper-proof. They help in audits and compliance checks. Businesses can trust the integrity of their data.
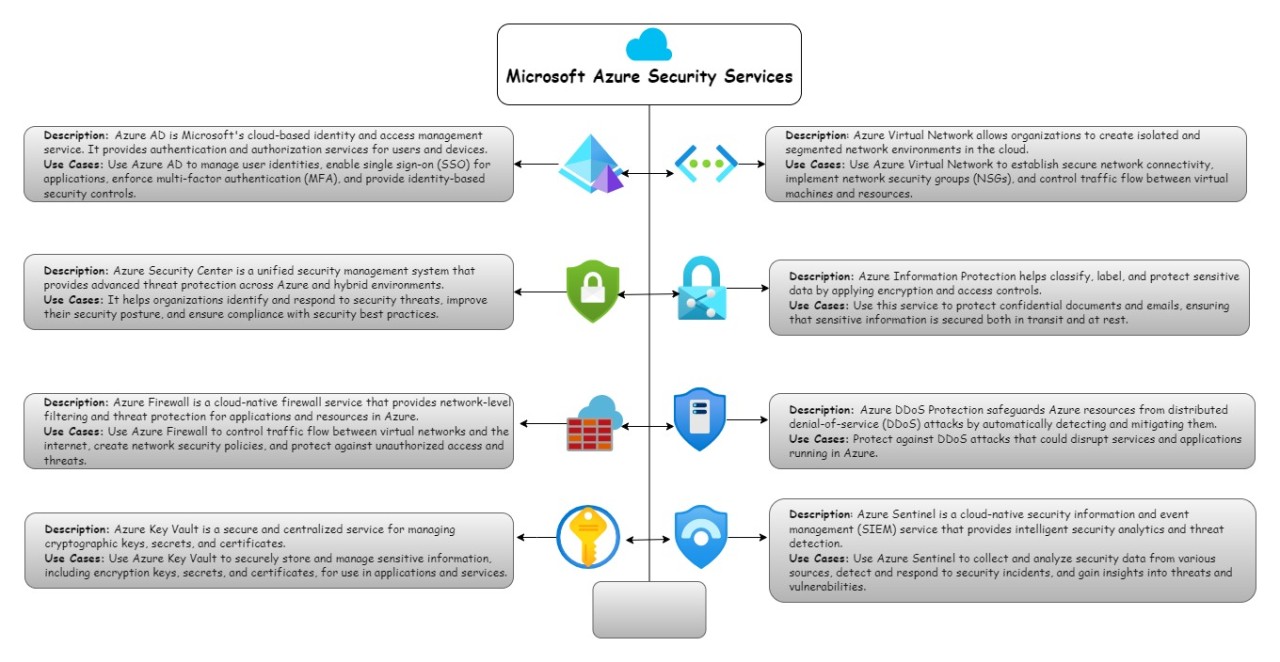
Credit: www.linkedin.com
Best Practices For Secure Cloud Connectivity
Cloud environments require strong security measures. Proper connectivity is vital for protecting sensitive data. Here are best practices to ensure secure cloud access.
Secure Access Service Edge (sase) Model
The Secure Access Service Edge (SASE) model combines networking and security. It delivers protection directly to users, regardless of their location. This model includes:
- Cloud-native security tools
- Integrated networking functions
- Real-time threat detection
SASE provides secure access to cloud applications. It simplifies management and reduces latency. Organizations can implement SASE by following these steps:
- Assess current network architecture.
- Identify security gaps.
- Choose a SASE provider.
- Deploy the solution across all locations.
Zero Trust Network Access (ztna)
Zero Trust Network Access (ZTNA) is a security framework. It operates on the principle of “never trust, always verify.” ZTNA protects cloud resources by:
- Authenticating every user.
- Limiting access based on roles.
- Monitoring user activity continuously.
Implementing ZTNA involves the following steps:
- Define access policies based on roles.
- Use multi-factor authentication.
- Regularly review access permissions.
- Conduct security audits frequently.
Both SASE and ZTNA enhance cloud security. Organizations must adopt these models to protect their data.
Incident Response And Recovery In Cloud Networks
Cloud networks face unique challenges. A strong incident response plan is vital. Quick recovery helps protect data and maintain trust. Understanding how to respond can minimize damage.
Developing A Robust Incident Response Plan
A solid incident response plan outlines steps to take during a security event. This plan should be clear and easy to follow. Key elements include:
- Identification: Detect incidents quickly.
- Containment: Limit the damage.
- Eradication: Remove the threat.
- Recovery: Restore systems.
- Lessons Learned: Analyze the incident.
Assign roles and responsibilities. Make sure your team knows their tasks. Regularly test the plan. Update it based on new threats.
| Phase | Description |
|---|---|
| Identification | Recognize potential incidents quickly. |
| Containment | Stop the incident from spreading. |
| Eradication | Remove malicious elements. |
| Recovery | Bring systems back online safely. |
| Lessons Learned | Review and improve the response plan. |
Disaster Recovery Strategies: Ensuring Business Continuity
Disaster recovery focuses on restoring operations after an incident. It ensures business continuity. Strategies include:
- Data Backup: Regularly back up data in multiple locations.
- Cloud-Based Recovery: Use cloud services for quick recovery.
- Redundancy: Implement redundant systems and networks.
- Testing: Regularly test disaster recovery plans.
Utilizing these strategies helps organizations recover faster. It reduces downtime and protects assets. A well-prepared business can adapt to unexpected events.

Credit: securityintelligence.com
Case Studies: Successful Cloud Security Implementations
Many companies have successfully enhanced their cloud security. They adopted effective solutions to protect their data. Let’s explore their stories and learn from their experiences.
Lessons From Companies With Robust Cloud Security
Several organizations have set benchmarks in cloud security. Here are key lessons from these leaders:
- Regular Security Audits: Frequent audits help identify vulnerabilities.
- Employee Training: Staff awareness reduces human errors.
- Multi-Factor Authentication: This adds an extra layer of protection.
- Data Encryption: Encrypting data secures sensitive information.
Analyzing The Impact Of Comprehensive Security Solutions
Companies that implemented complete security solutions saw significant benefits. Here’s a summary:
| Company | Security Solution | Impact |
|---|---|---|
| Company A | End-to-End Encryption | Reduced data breaches by 80% |
| Company B | Automated Threat Detection | Identified threats 70% faster |
| Company C | Comprehensive Training Programs | Decreased phishing incidents by 50% |
These organizations demonstrate the importance of comprehensive solutions. They protect data and enhance overall security. Their success stories inspire others to follow suit.
Future Of Cloud Network Security
The future of cloud network security looks promising yet challenging. As more businesses move to cloud solutions, security must keep pace. New technologies will emerge to protect data and systems. Understanding trends helps organizations prepare for what lies ahead.
Predicting Trends And Innovations
Cloud network security will see several key trends in the coming years:
- AI and Machine Learning: These technologies will enhance threat detection.
- Zero Trust Security: This model assumes no user is trustworthy.
- Increased Compliance: Regulations will tighten around data protection.
- Enhanced Encryption: Stronger encryption methods will safeguard data.
Organizations must adopt these innovations to stay ahead. AI can analyze vast amounts of data. This helps identify threats faster than humans. Zero Trust Security requires strict identity verification.
| Trend | Description |
|---|---|
| AI and Machine Learning | Automated threat detection and response. |
| Zero Trust Security | Verifying every user and device. |
| Increased Compliance | Meeting stricter data protection laws. |
| Enhanced Encryption | Improved methods for securing data. |
Preparing For Emerging Security Threats
Organizations must prepare for new types of threats. Cybercriminals are becoming more sophisticated. Here are some steps to take:
- Regular Security Audits: Assess your security posture often.
- Employee Training: Educate staff on security best practices.
- Incident Response Plan: Have a clear plan for security breaches.
- Use Multi-Factor Authentication: Add an extra layer of security.
Staying informed about emerging threats is vital. New threats can appear quickly. Proactive measures can prevent significant damage.
Conclusion: Fortifying Your Cloud Environment
Securing your cloud environment is essential for data safety. Cloud-based systems face unique threats. Implementing strong network security solutions helps protect sensitive information.
Summarizing Key Takeaways
- Identify vulnerabilities: Regularly assess your cloud environment.
- Use firewalls: Deploy virtual firewalls for better security.
- Encrypt data: Protect data at rest and in transit.
- Implement access controls: Limit user permissions based on roles.
- Monitor traffic: Use tools to track unusual activities.
Next Steps For Implementing Network Security Solutions
- Conduct a security audit of your cloud environment.
- Select appropriate security tools based on your needs.
- Train staff on security best practices.
- Establish an incident response plan.
- Regularly update security protocols and tools.
Prioritize security in your cloud strategy. Protecting data ensures business continuity. Stay informed about new threats and solutions.
Frequently Asked Questions
What Are Cloud Network Security Solutions?
Cloud network security solutions are strategies and tools designed to protect data and applications hosted in cloud environments. These solutions ensure data integrity, confidentiality, and availability while combating threats like malware and unauthorized access. They often include firewalls, encryption, and identity management systems to safeguard cloud resources.
Why Is Cloud Security Important?
Cloud security is crucial because it protects sensitive information stored online. With increasing cyber threats, organizations must secure their cloud environments to prevent data breaches. Effective cloud security ensures compliance with regulations, safeguards customer trust, and mitigates financial losses from potential attacks.
How To Choose The Right Cloud Security Solution?
Choosing the right cloud security solution involves assessing your organization’s specific needs. Consider factors like data sensitivity, compliance requirements, and existing infrastructure. Evaluate solutions based on scalability, user-friendliness, and integration capabilities. Always look for providers with strong customer support and proven track records in the industry.
What Are Common Cloud Security Threats?
Common cloud security threats include data breaches, account hijacking, and insecure APIs. Other risks involve insider threats and insufficient access controls. Understanding these threats is essential for implementing robust security measures. Regular assessments and updates can help mitigate these risks effectively.
Conclusion
Effective network security solutions are essential for protecting cloud-based environments. Implementing robust strategies mitigates risks and safeguards sensitive data. Organizations must prioritize ongoing assessments and updates to their security measures. By staying proactive, businesses can navigate the complexities of cloud security and ensure their digital assets remain secure against evolving threats.




Leave a Reply